Microsoft announces the public preview of Watchlist feature in Azure Sentinel
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
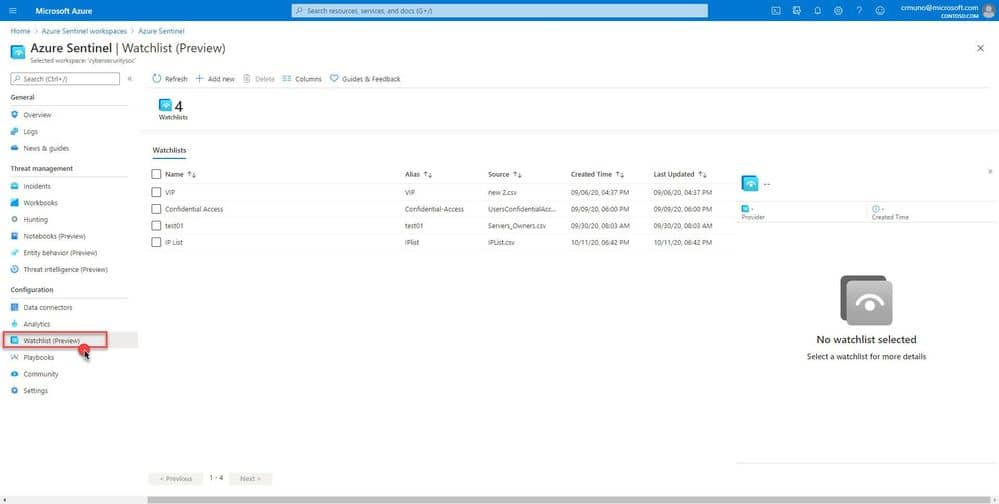
Back in 2019, Microsoft announced Azure Sentinel, a native Security Information and Event Management (SIEM) tool built within Azure. It allowed SecOps teams to see and stop threats before they cause any harm to the organizations. Microsoft today announced the public preview of Watchlist feature in Azure Sentinel.
Azure Sentinel watchlists will enable the collection of data from external data sources for correlation against the events in an Azure Sentinel environment. SecOps teams can use watchlists in their search, detection rules, threat hunting and response playbooks. The new watchlists feature can be used in the following scenarios:
- Investigate threats and respond to incidents quickly with fast import of IP addresses, file hashes, etc. from csv files. Then utilize the watchlist name/value pairs for joining and filtering for use in alert rules, threat hunting, workbooks, notebooks and for general queries.
- Import business data, such as user lists with privileged system access as a watchlist. Then use the watchlist to create allow and deny lists. For example, use a watchlist that contains a list of terminated employees to detect or prevent them from logging in to the network.
- Create allow-lists to reduce alert fatigue. For example, use a watchlist to build an allow list to suppress alerts from only a limited set of IP addresses to do specific functions and thus removing benign events from becoming alerts.
- Use watchlists to enrich your event data with field-value combinations derived from external data sources.
Source: Microsoft






User forum
0 messages