OMIGOD ! Microsoft left a big RCE hole in their default Linux configuration on Azure
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
Microsoft says they love Linux, but it seems that love did not extend to ensuring they did not give super-easy root access to hackers for Azure installations of the OS.
Security company Wiz’s research team recently discovered a series of alarming vulnerabilities in the little-known software agent called Open Management Infrastructure (OMI) that’s embedded in many popular Azure services.
When customers set up a Linux virtual machine in their cloud, including on Azure, the OMI agent is automatically deployed without their knowledge when they enable certain Azure services. Unless a patch is applied, attackers can easily exploit four vulnerabilities to escalate to root privileges and remotely execute malicious code (for instance, encrypting files for ransom).
All hackers have to do to gain root access on a remote machine is sent a single packet with the authentication header removed.
If OMI externally exposes ports 5986, 5985, or 1270 then the system is vulnerable.
“Thanks to the combination of a simple conditional statement coding mistake and an uninitialized auth struct, any request without an Authorization header has its privileges default to uid=0, gid=0, which is root.”
Wiz dubbed the vulnerability OMIGOD and believes up to 65% of Linux installations on Azure were vulnerable.
Microsoft released a patched OMI version (1.6.8.1). In addition, Microsoft advised customers to manually update OMI, see the suggested steps by Microsoft here.
Wiz suggests if you have OMI listening on ports 5985, 5986, 1270 to limit network access to those ports immediately in order to protect from the RCE vulnerability (CVE-2021-38647).
via ZDNet
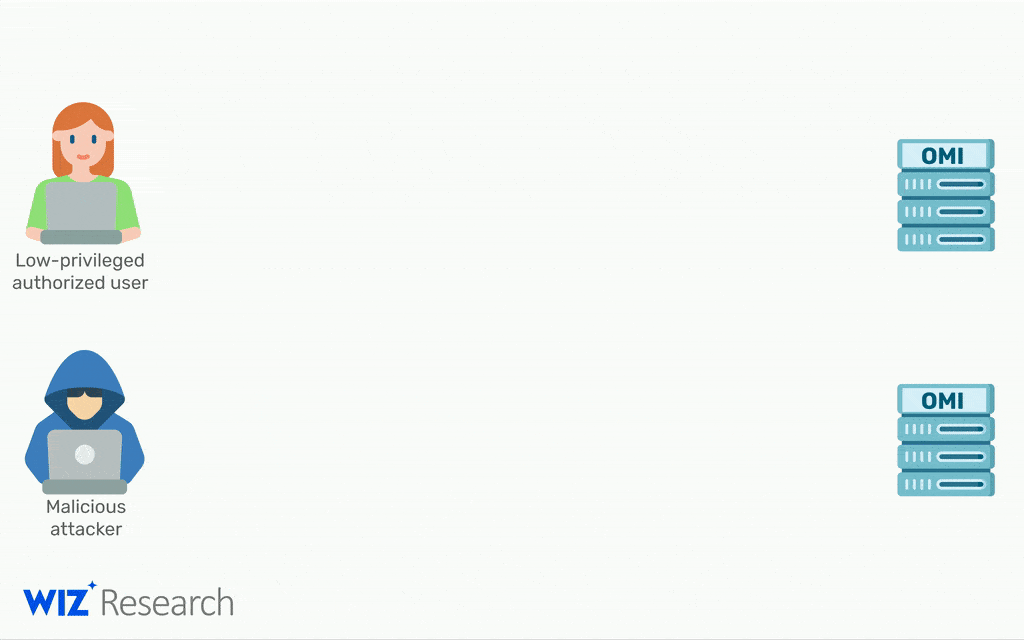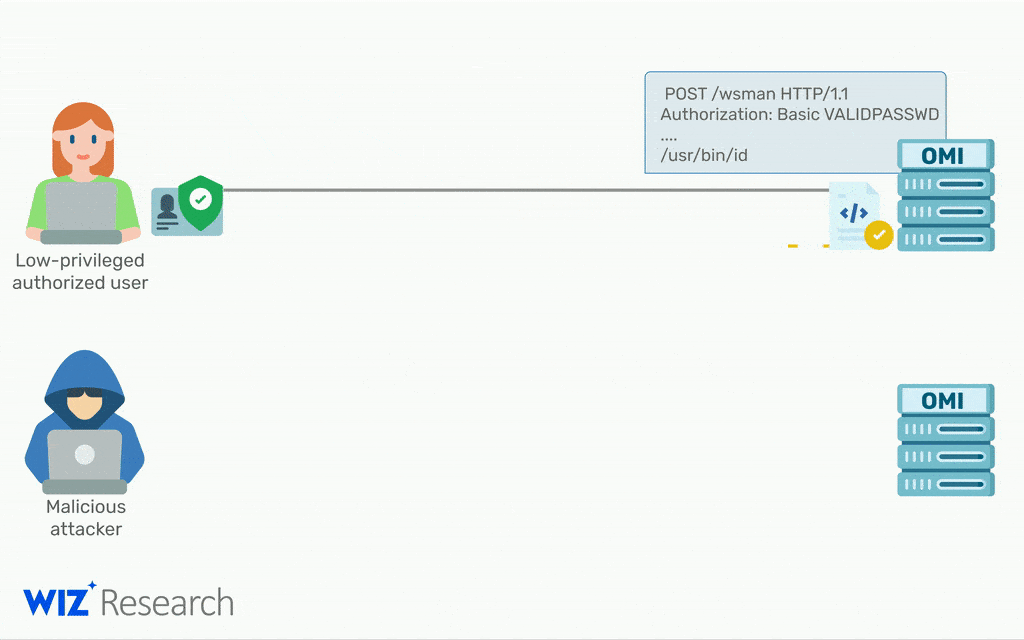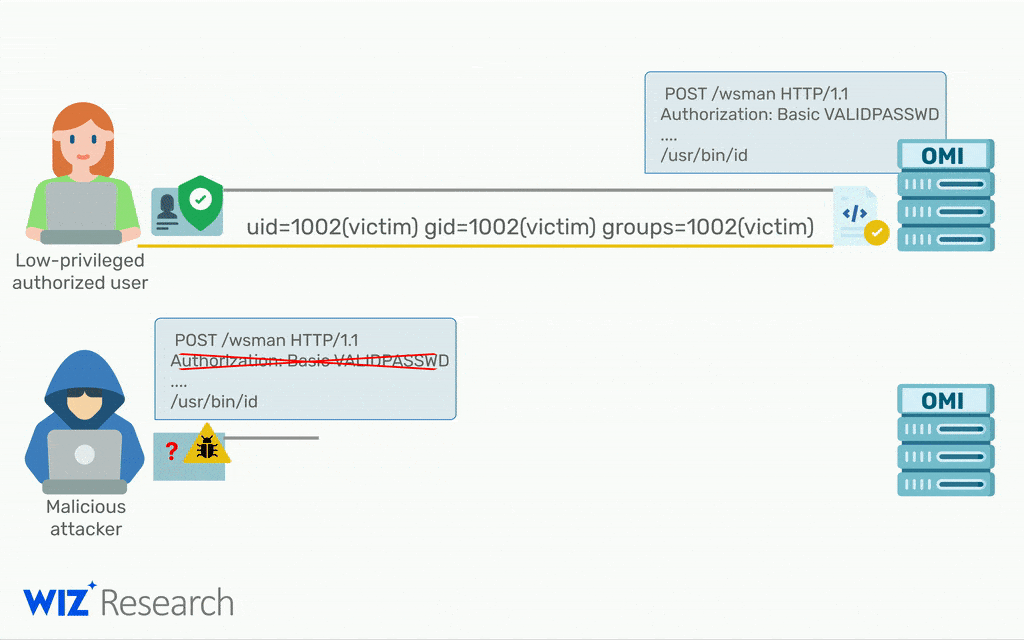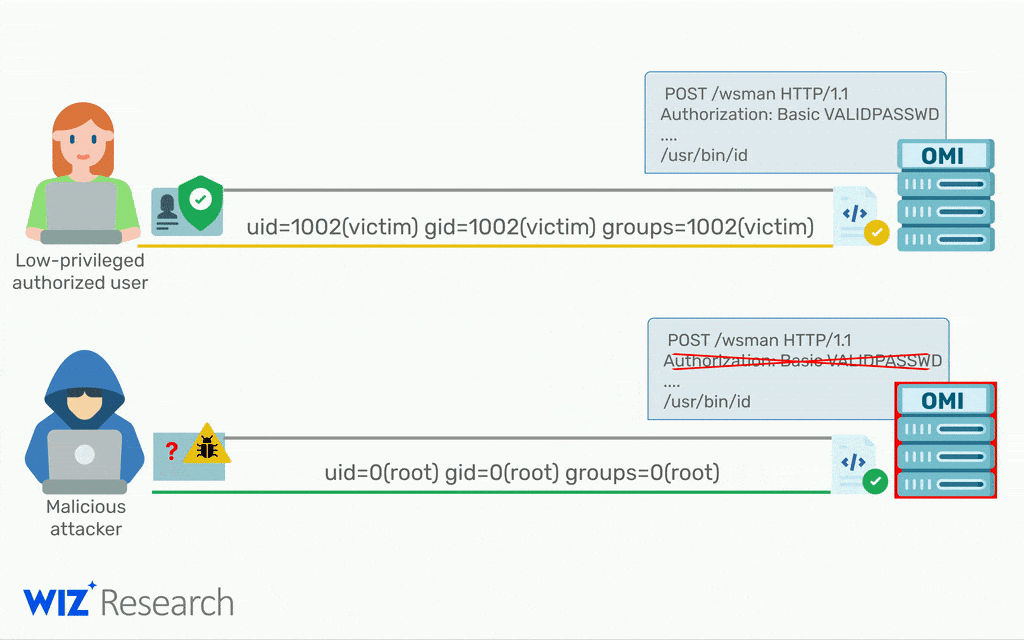







User forum
0 messages