0day release a micro-patch for Windows 7 zero-day vulnerability
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
Unless you have an Extended Security Update contract most Windows 7 users are no longer receiving patches from Microsoft.
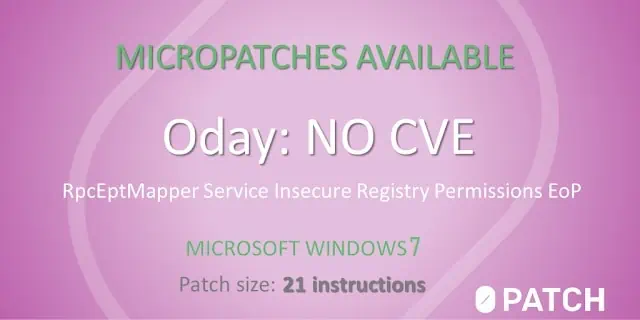
Unfortunately, nearly 1 in 4 Windows users are still running Windows 7, and a recently discovered local privilege escalation vulnerability (which also affects Windows Server 2008 R) means your installation is no longer secure.
In short, the vulnerability is that all local users have write permissions on two registry keys:
HKLM\SYSTEM\CurrentControlSet\Services\Dnscache
HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper
Windows Performance Monitoring mechanism can be made to read from these keys – and eventually load the DLL provided by the local attacker, running it as Local System.
To exploit the vulnerability a local non-admin user on the computer simply needs to create a Performance subkey in one of the above keys, populates it with some values, and triggers performance monitoring, which leads to a Local System WmiPrvSE.exe process loading attacker’s DLL and executing code from it.
Fortunately for admins of Windows 7 networks (once again 1/4 of Windows PCs in the wild) 0patch have “security adopted” Windows 7 and Windows Server 2008 R2 and are providing critical security patches for the platforms.
They analysed the flaw and found OpenExtensibleObjects iterates through all services in the registry looking for Performance keys, and they decided to patch it so that it would ignore this key in both affected services – making it look as if the Performance key wasn’t there even if it was.
This does break performance monitoring for the affected services. In case performance monitoring is needed for these services, the micropatch can always be temporarily disabled without restarting of the service or computer.
This micropatch is immediately available to all 0patch users, including those with a FREE 0patch plan. It is targeted at:
Windows 7 and Server 2008 R2 computers without ESU, updated to January 2020, and Windows 7 and Server 2008 R2 computers with ESU, updated to November 2020.
The micropatch is free for everyone until Microsoft issues an official fix for it. Read all the details at opatch here.







User forum
0 messages