Zoom vulnerability released which allows anyone you chat with to steal your Windows Login credentials
3 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
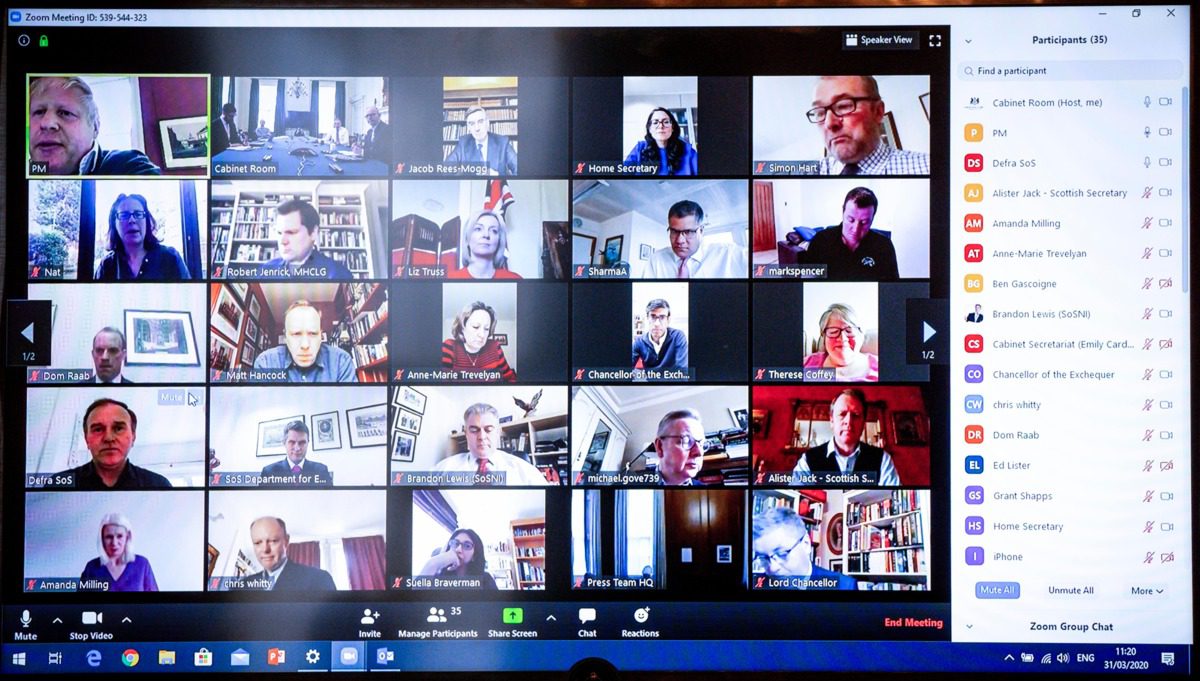
Zoom has rapidly, well, zoomed to prominence during the COVID-19 crisis as an easy to use video chat client, and it is currently being used in the highest corridors of power, such as by the British Priminister and his cabinet.
Unfortunately, all that haste and ease of use has meant the client is not that robust to hacking. Previous issues have included malicious websites being able to start video calls without user interaction and the lack of full encryption of video.
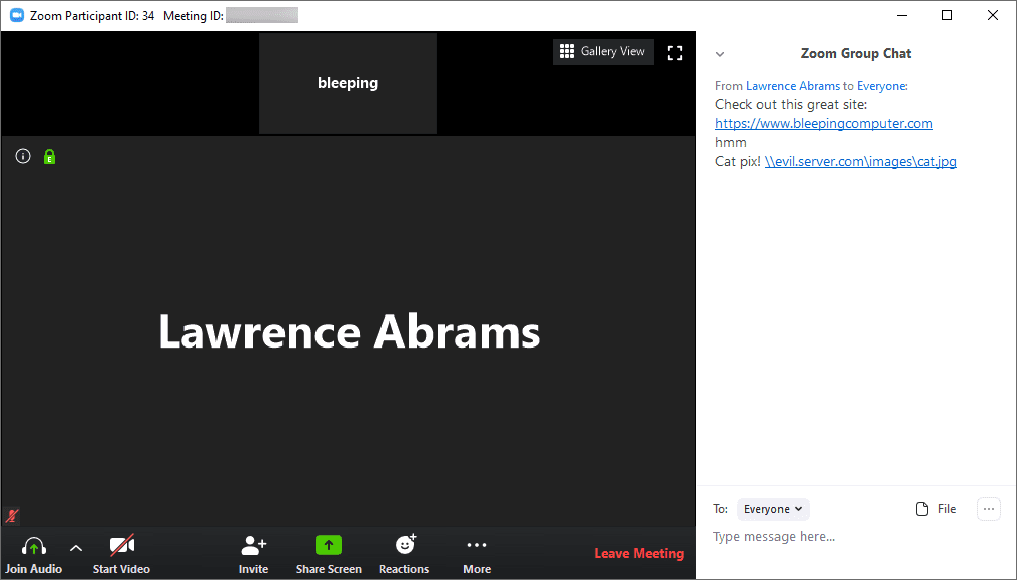
A new, easy to exploit vulnerability has been disclosed which means hackers can easily steal the Windows username and password of participants if they click on a malicious link in the chat window.
The issue is that Zoom automatically converts links into clickable links, including network paths.
When chat participants click on those links, Windows automatically tries to log in to that network share, sending your username and NTLM password hash, which can easily be cracked using free tools like Hashcat in seconds.
With Zoom bombing meaning that strangers could easily join large sessions, the issue could easily compromise some very important computer and networks.
Zoom, who has been informed of the issue, can fix the issue by not turning network paths into clickable links, while network admins in the meantime can disable the automatic sending of network login credentials via the group policy ‘Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers’, though this can cause issues when accessing resources on some networks.
Home users can modify the RestrictSendingNTLMTraffic Registry value under the HKEY_LOCAL_MACHINE\ SYSTEM\CurrentControlSet\ Control\Lsa\MSV1_0 key and set it to 2. They do not need to reboot.
While we wait for a fix, read more about this mitigation at BleepingComputer here.
Update 1:
Another Zoom security flaw has been discovered. Zoom is leaking email addresses, user photos, and allowing some users to initiate a video call with strangers. This is because of how the app handles contacts that it perceives work for the same organization. Read about it in detail here.
Update 2:
Over the next 90 days, Zoom will be using all its resources to better identify, address, and fix security and privacy issues proactively. So, Zoom won’t be adding any new features in the next 3 months. It will also conduct a comprehensive review with third-party experts and representative users to understand and ensure the security of its service. Learn more about this announcement here.




User forum
0 messages