Windows Hello authentication bypassed with fake camera
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

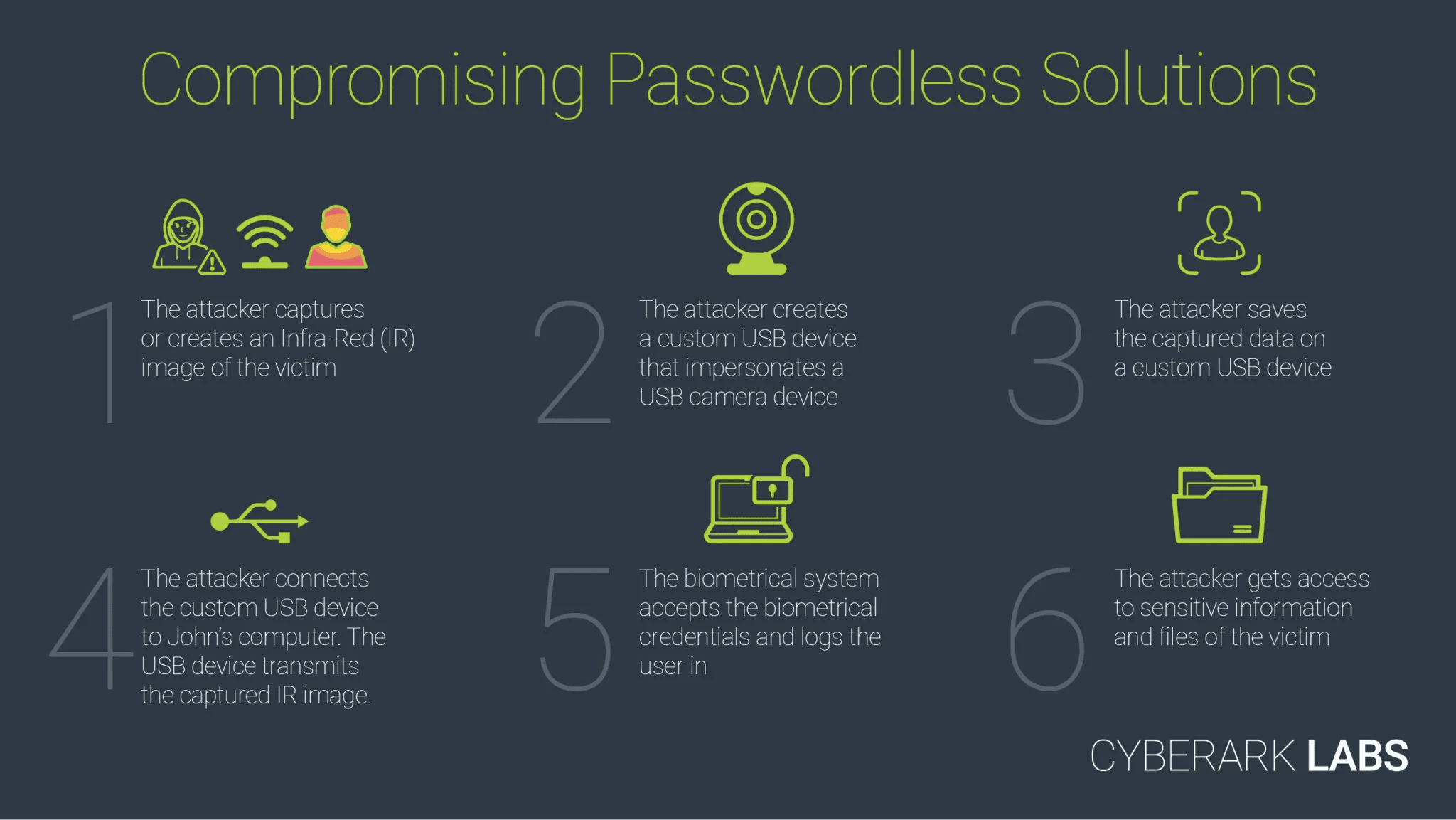
Hackers have demonstrated that they are able to bypass Windows Hello security by using a fake USB camera that transmitted captured infra-red pictures of a target which it appears Windows Hello is quite happy to accept.
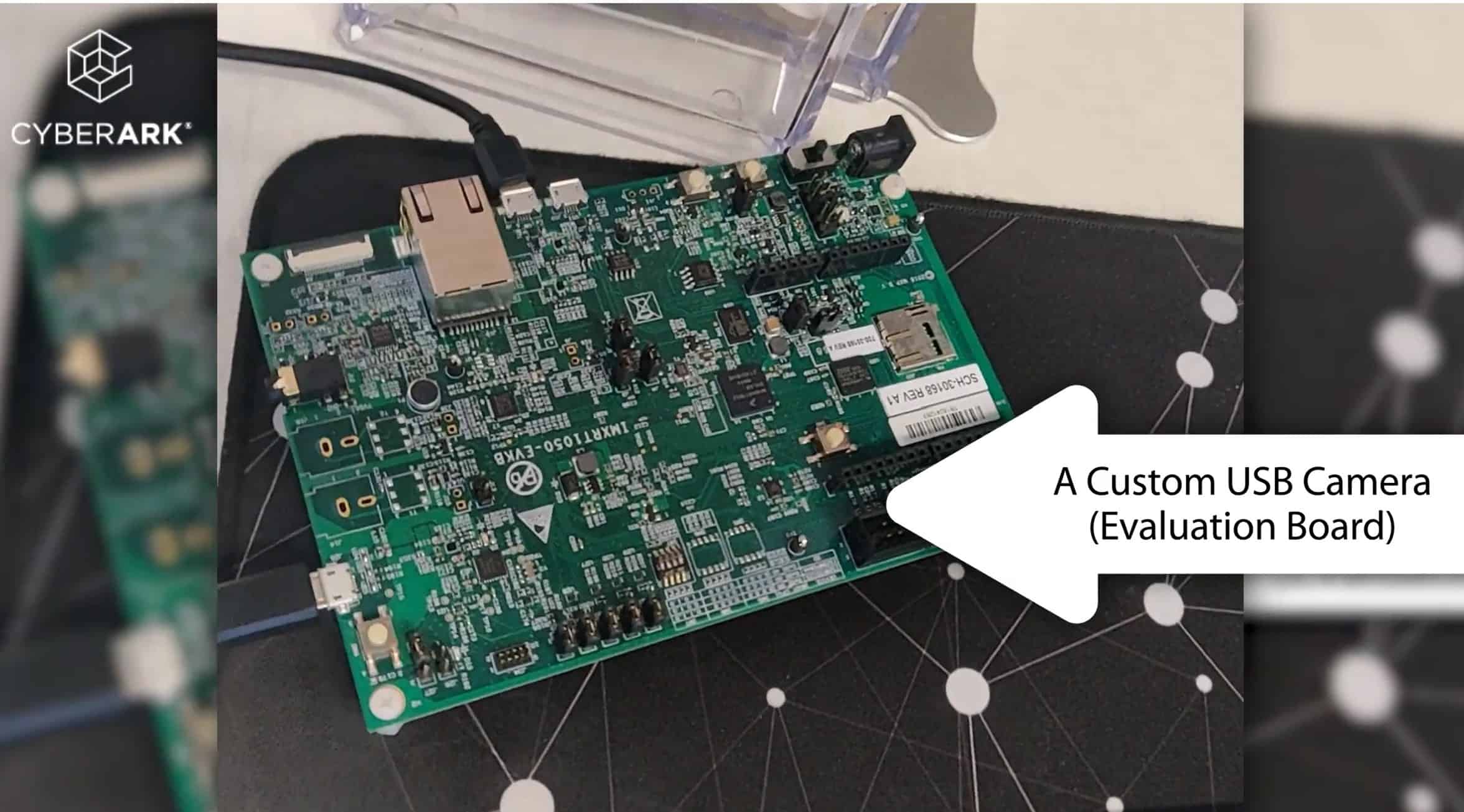
The issue appears to be Windows Hello’s willingness to accept any IR-capable camera as a Windows Hello camera, allowing hackers to offer a manipulated rather than real data steam to the PC.
In addition, it turns out hackers only have to send two frames to the PC – one real IR capture of the target, and one blank black frame. It appears the second frame is needed to fool Windows Hello’s liveness tests.
CyberArk Labs says the IR image can be captured by special long-range IR cameras or by cameras placed surreptitiously in the environment of the target, such as a lift.
Microsoft has recognized the vulnerability in an advisory CVE-2021-34466 and has offered Windows Hello Enhanced Sign-in Security as mitigation. This only allows Windows Hello cameras which are part of the cryptographic chain of trust from the OEM to be used as a source of data, something which CyberArk notes is not supported by all devices.
Read all the detail at CyberArk here.








User forum
0 messages