Beware of this new Tycoon ransomware targeting Windows PCs
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
FBI Internet Crime Complaint Center (IC3) last year published the “Internet Crime Report”. The report revealed that cybercrime had cost a massive $3.5 billion (£2.7 billion) in 2019. Attackers use ransomware to extract money from businesses and individual users. BlackBerry’s security research unit recently discovered a new ransomware that affected an European educational institute. Unlike most of the ransomware discovered till date, this new ransomware module is compiled into a Java image file format (JIMAGE). JIMAGE is a file format that stores custom JRE images which is designed to be used by the Java Virtual Machine (JVM) at runtime.
Here’s how the attack happened:
- To achieve persistence on the victim’s machine, the attackers had used a technique called Image File Execution Options (IFEO) injection. IFEO settings are stored in the Windows registry. These settings give developers an option to debug their software through the attachment of a debugging application during the execution of a target application.
- A backdoor was then executed alongside the Microsoft Windows On-Screen Keyboard (OSK) feature of the operating system.
- The attackers disabled the organization’s anti-malware solution with the use of the ProcessHacker utility and changed the passwords for Active Directory servers. This leaves the victim unable to access their systems.
- Most of the attacker files were timestomped, including the Java libraries and the execution script, and had file date timestamps of 11th April 2020, 15:16:22
- Finally, the attackers executed the Java ransomware module, encrypting all file servers including backup systems that were connected to the network.
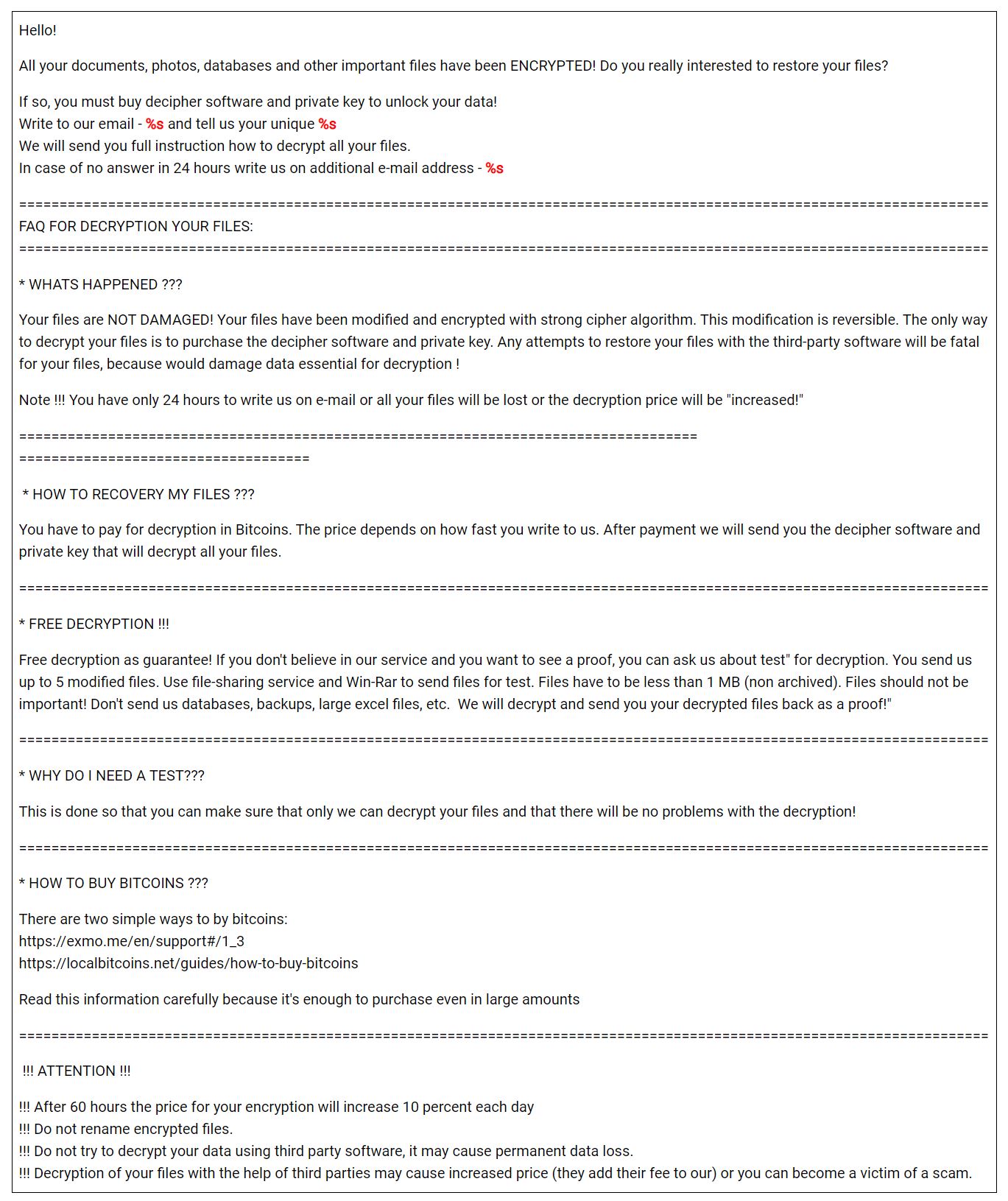
After extraction of the zip file associated with the ransomware, there are three modules in the name of “tycoon”. So, Blackberry team has named this ransomware as tycoon. Check out the ransom note of tycoon below.
You can find more details about this ransomware from the link below.
Source: Blackberry