New PrintNightmare hack means any user can gain admin privileges on their PC
2 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
Microsoft’s PrintNightmare refuses to end, with another version of the hack meaning any user can gain admin privileges on their PC, even from a limited account.
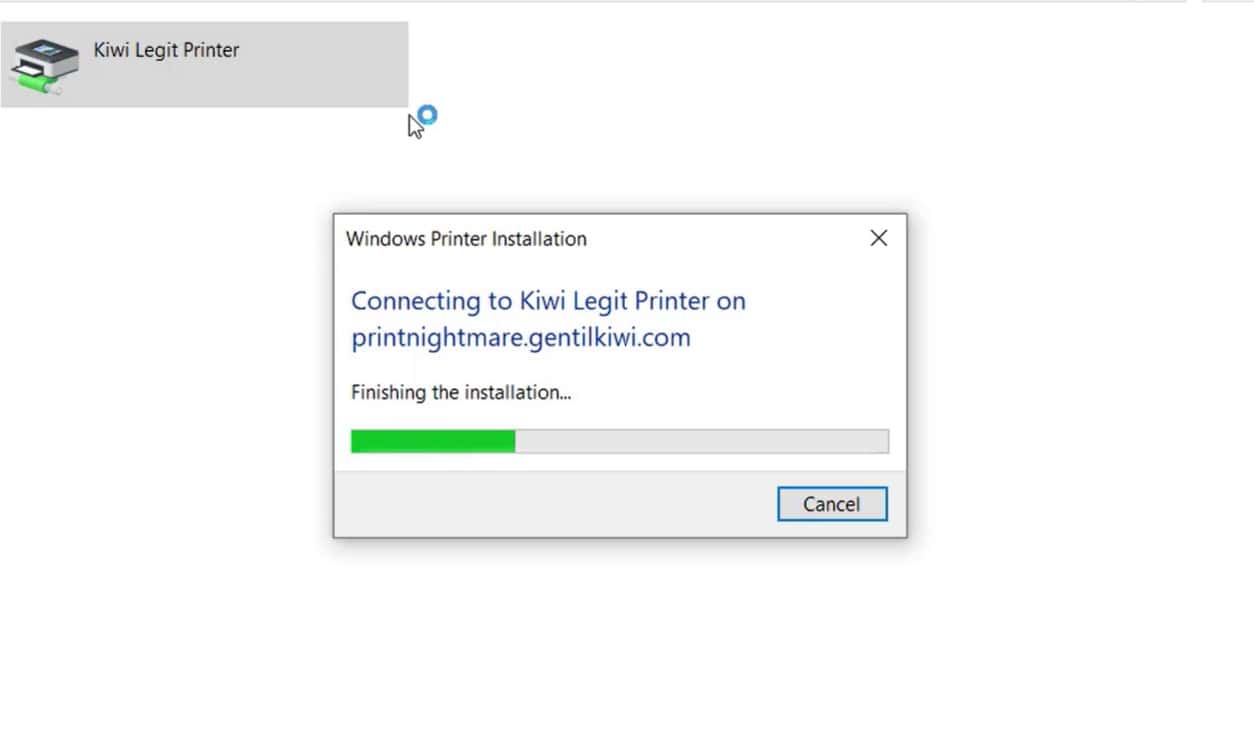
The hack was developed by Benjamin Delpy and takes advantage of the fact that Windows is pretty happy to install drivers from remote print servers and run those drivers at System privilege level, and that even Limited users can install remote printers.
Want to test #printnightmare (ep 4.x) user-to-system as a service??
(POC only, will write a log file to system32)connect to \https://t.co/6Pk2UnOXaG with
– user: .gentilguest
– password: passwordOpen 'Kiwi Legit Printer – x64', then 'Kiwi Legit Printer – x64 (another one)' pic.twitter.com/zHX3aq9PpM
— ????? Benjamin Delpy (@gentilkiwi) July 17, 2021
He has set up a remote printer server at \\printnightmare[.]gentilkiwi[.]com which downloads a hacked driver which opens a system prompt, meaning corporate users or hackers with access to a limited account can now easily elevate privileges and gain complete control of their PC.
BleepingComputer tested the hack on a fully patched PC running Windows 10 21H1, and except for the malicious driver being detected by Windows Defender, the exploit worked smoothly as intended.
Until Microsoft fixes the issue mitigation is rather difficult, ranging from disabling the Print Spooler and basically all printing to creating a custom list of remote printers which users are allowed to install.
Read more about the hack and possible mitigation at BleepingComputer here.








User forum
0 messages