Microsoft's new Azure Information Protection Public Preview now available to download
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
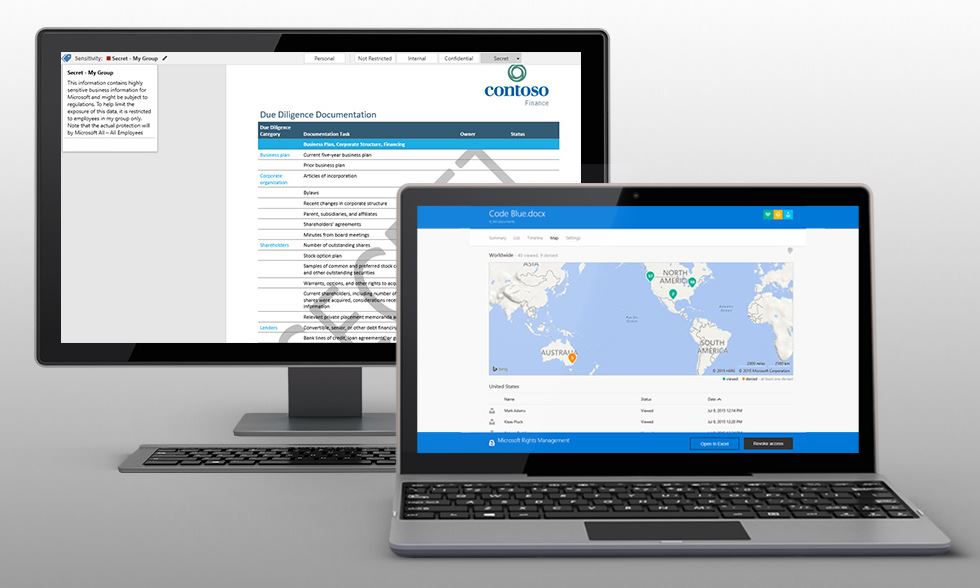

Last month Microsoft announced the launch of the Microsoft Azure Information Protection service that builds on existing Microsoft Azure Rights Management (Azure RMS) and their recent acquisition of Secure Islands. They have now combined Secure Islands’ industry-leading data classification and labeling technology with Azure RMS, and have released a public preview of Azure Information Protection to download and try out
Microsoft Azure Information Protection deliver these key capabilities:
- Classify, label and protect data at the time of creation or modification. Use policies to classify and label data in intuitive ways based on the source, context and content of the data. Classification can be fully automatic, user-driven or based on a recommendation. Once data is classified and labeled, protection can be applied automatically on that basis.
- Persistent protection that travels with your data. Classification and protection information travels with the data. This ensures that data is protected at all times, regardless of where it is stored, with whom it is shared, or if the device is running iOS, Android or Windows.
- Enable safe sharing with customers and partners. Share data safely with users within your organization as well as with external customers and partners. Document owners can define who can access data and what they can do with it; for example, recipients can view and edit files, but they cannot print or forward.
- Simple, intuitive controls help users make the right decisions and stay productive. Data classification and protection controls are integrated into Office and common applications. These provide simple one-click options to secure data that users are working on. In-product notifications provide recommendations to help users make the right decisions.
- Visibility and control over shared data. Document owners can track activities on shared data and revoke access when necessary. IT can use logging and reporting to monitor, analyze and reason over shared data.
- Deployment and management flexibility. Protect data whether it is stored in the cloud or on-premises, and choose how your encryption keys are managed with Bring Your Own Key options.
Video demo:
Check out their website to learn more and download the preview from Microsoft here.


User forum
0 messages