Here is how to protect your network against the PetitPotam relay attack
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
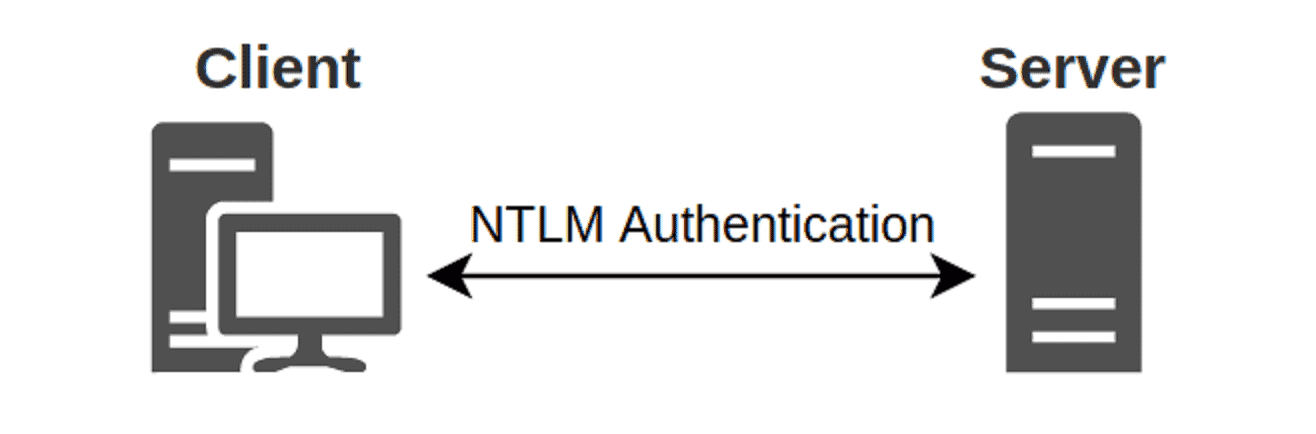
A new security issue has been troubling corporate network administrators after French security researcher Gilles Lionel disclosed a new NTLM relay attack that allows hackers to take over the domain controller or other Windows servers.
Named PetitPotam, the attack was disclosed a few days ago, allow with Proof of Concept code.
Hi all,
MS-RPRN to coerce machine authentication is great but the service is often disabled nowadays by admins on most orgz.
Here is one another way we use to elicit machine account auth via MS-EFSRPC. Enjoy!! 🙂https://t.co/AGiS4f6yt8— topotam (@topotam77) July 18, 2021
The exploit uses Microsoft Encrypting File System Remote Protocol (EFSRPC) to force a device, including domain controllers, to authenticate to a malicious remote NTLM relay, which can then be used to steal hash and certificates and assume the identity of the actual device and its privileges.
Microsoft is not overly alarmed, however, saying:
Microsoft is aware of PetitPotam which can potentially be used in an attack on Windows domain controllers or other Windows servers. PetitPotam is a classic NTLM Relay Attack, and such attacks have been previously documented by Microsoft along with numerous mitigation options to protect customers. For example, see Microsoft Security Advisory 974926.
To prevent NTLM Relay Attacks on networks with NTLM enabled, domain administrators must ensure that services that permit NTLM authentication make use of protections such as Extended Protection for Authentication (EPA) or signing features such as SMB signing. PetitPotam takes advantage of servers where Active Directory Certificate Services (AD CS) is not configured with protections for NTLM Relay Attacks. The mitigations outlined in KB5005413 instruct customers on how to protect their AD CS servers from such attacks.
You are potentially vulnerable to this attack if NTLM authentication is enabled in your domain and you are using Active Directory Certificate Services (AD CS) with any of the following services:
- Certificate Authority Web Enrollment
- Certificate Enrollment Web Service
The simple solution is therefore to disable NTLM where it is not necessary, e.g. Domain Controllers, or to enable the Extended Protection for Authentication mechanism or enable NTLM authentication to use signing features such as SMB signing.
Like PrintNightmare, this may be only the first chapter in the PetitPotam saga, since Gilles Lionel told BleepingComputer that PetitPotam allows other atacks, such as a downgrading attack to NTLMv1 that uses the Data Encryption Standard (DES) – an insecure algorithm due to its short, 56-bit key generation that makes it easy to recover a password hash, allowing for a local privilege escalation attack.
Microsoft has also not addressed the EFSRPC protocol used in the attack.
Read Microsoft’s advisory here, and more at BleepingComputer.








User forum
0 messages