Hackers use Mailchimp’s internal tool to access customer accounts
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

Mailchimp experienced a data breach after hackers had managed to access the company’s internal tool. Being a marketing automation platform and email marketing service giant, it spelled catastrophe to its clients. One of the affected businesses is the open-source security hardware company Trezor, which announced the issue in a Twitter post and warned its clients.
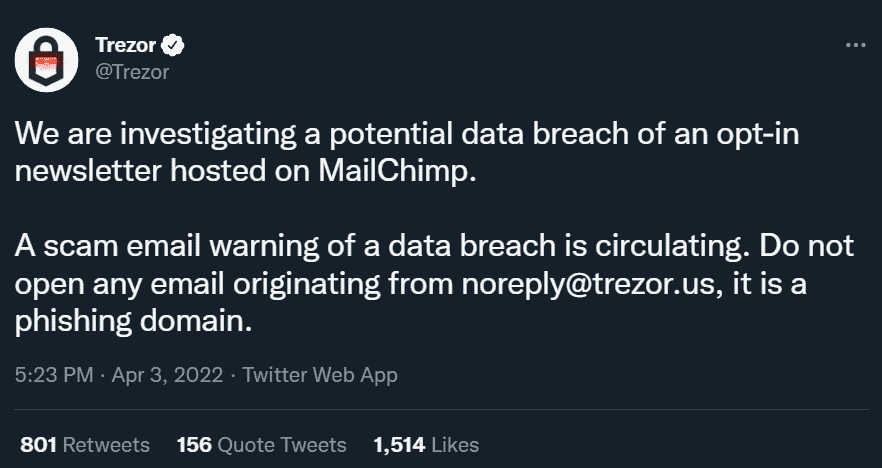
“We are investigating a potential data breach of an opt-in newsletter hosted on MailChimp,” reads the post. “A scam email warning of a data breach is circulating. Do not open any email originating from [email protected], it is a phishing domain.”
The breach happened after a social engineering attack that fooled victims with malicious activity to gain access. According to the statement Mailchimp CISO Siobhan Smyth provided to Techcrunch, Mailchimp identified the problem after it saw the malicious actor utilizing the tool of the company’s account administration and customer support teams last March 26.
Smyth said that the company “acted swiftly to address the situation by terminating access for the compromised employee accounts and took steps to prevent additional employees from being affected.” However, despite the assurance given, Mailchimp admitted that the bad actors already had their hands on roughly 300 accounts, with 102 of them experienced audience data export. Though Mailchimp didn’t detail the types of data acquired, it was said that the activity was executed to target the finance and cryptocurrency companies. This somehow explains the post of Trezor, a cryptocurrency wallet maker, that uses Mailchimp to send newsletters to its customers. As mentioned in its post, Trezor warned its users not to open malicious emails from a specific sender. The emails would push users to reset their hardware wallet PINs through a download of malicious software. Once installed, malicious actors would be able to access users’ cryptos and steal them.
During the execution of the crime, the hackers also got access to other API keys that could allow them to send forged emails. Mailchimp already disabled them to prevent further usage; however, the company also received reports that the hackers are still using the stolen information of users to perform phish their contacts.
“When we become aware of any unauthorized account access, we notify the account owner and immediately take steps to suspend any further access,” Smyth told TechCrunch. “We also recommend two-factor authentication and other account security measures for our users as added measures to keep accounts and passwords secure.”








User forum
0 messages