Microsoft warns M365 users of growing phishing crimes in new Digital Defense Report
4 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

The latest Microsoft Digital Defense Report 2022 says credential phishing schemes are increasing and reveals it is one of the biggest threats online. The crime targets all inboxes from different individuals around the globe, but one of the biggest prey being eyed by operators are those who have Microsoft 365 credentials, the report adds.
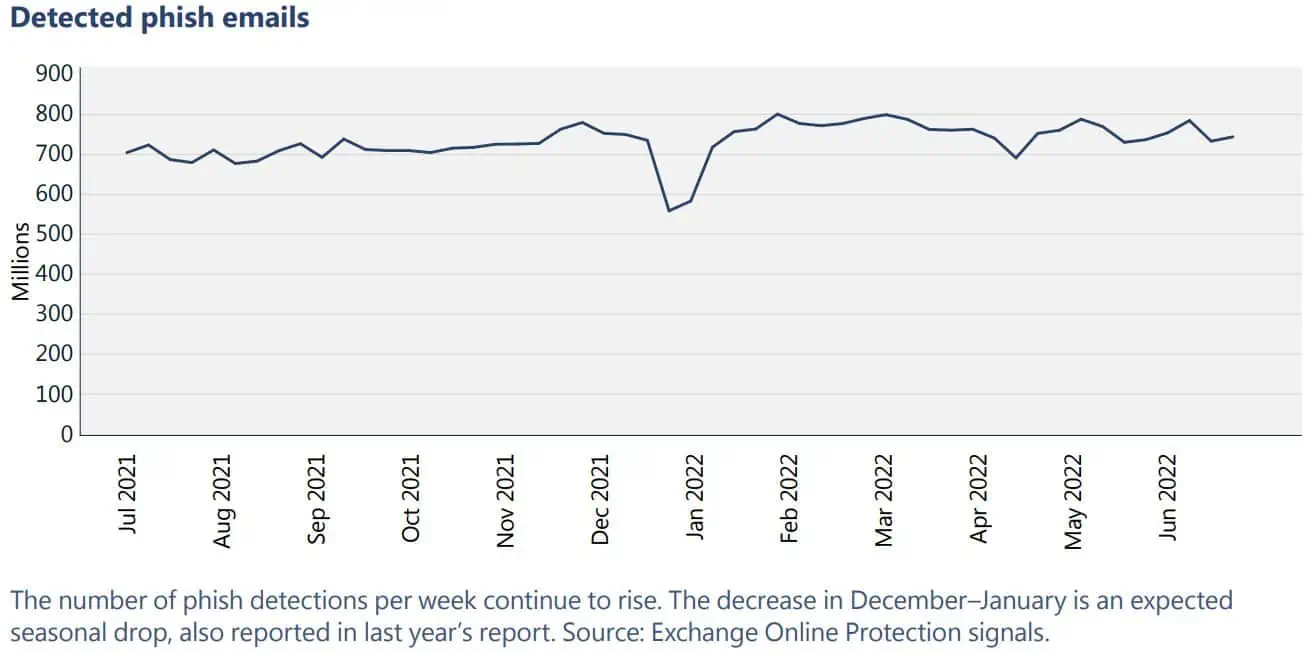
“Microsoft 365 credentials remain one of the most highly sought-after account types for attackers,” Microsoft explains in its report. “Once login credentials are compromised, attackers can log in to corporate-tied computer systems to facilitate infection with malware and ransomware, steal confidential company data and information by accessing SharePoint files, and continue the spread of phish by sending additional malicious emails using Outlook, among other actions.”
According to the Redmond company, the conclusion came from the data gathered from its various resources, including Defender for Office, Azure Active Directory Identity Protection, Defender for Cloud Apps, Microsoft 365 Defender, and Defender for Endpoint. Through this, Microsoft explained that it was able to spot and observe malicious email and compromised identity activity, compromised identity event alerts, compromised identity data access events, attack behavior alerts and events, and cross-product correlation.
Microsoft further warns the public of how serious phishing attacks are now, saying falling victim to a bait email translates to a median time of only one hour and 12 minutes for the attacker to access the victim’s private data. Likewise, once sensitive information is accessed, the median time would only take another 30 minutes for the criminal to move laterally within the victim’s corporate network.
Microsoft further warns everyone regarding numerous phishing landing pages disguised as Microsoft 365 login pages. According to the report, attackers are trying to copy the Microsoft login experience by producing customized URLs for each recipient or target.
“This URL points to a malicious webpage developed to harvest credentials, but a parameter in the URL will contain the specific recipient’s email address,” Microsoft expounds. “Once the target navigates to the page, the phish kit will prepopulate user login data and a corporate logo customized to the email recipient, mirroring the appearance of the targeted company’s custom Microsoft 365 login page.”
The Redmond company also underscores attackers’ usual activity of using prominent issues and events to make their operations more luring for victims. This includes the COVID-19 pandemic, the Ukraine-Russia war, and even the normalization of remote work, allowing attackers to design their operations around collaboration and productivity tools. In September, Proofpoint also shared that the death of Queen Elizabeth II was used by cybercriminals to disguise themselves as Microsoft. In the same month, Cofense said that a group of malicious actors tried to fool huge companies (particularly those in the energy, professional services, and construction sectors) into submitting their Microsoft Office 365 account credentials. According to the report, the actors used documents from the Departments of Transportation, Commerce, and Labor and designed their credential phishing pages to look more like the webpages of the said US government agencies.
In relation to this, Microsoft says businesses are valuable targets for phishing operators who use BEC attacks or email phishing attacks against businesses for financial gain. The report also discloses growing financial losses among different businesses due to the said crime, prompting the need for organizations to review their security protections.
“Microsoft detects millions of BEC emails every month, equivalent to 0.6 percent of all phishing emails observed. A report from IC3 published in May 2022 indicates an upward trend in exposed losses due to BEC attacks,” Microsoft reports. “The techniques used in phishing attacks continue to increase in complexity. In response to countermeasures, attackers adapt new ways to implement their techniques and increase the complexity of how and where they host campaign operation infrastructure. This means organizations must regularly reassess their strategy for implementing security solutions to block malicious emails and strengthen access control for individual user accounts.”









User forum
0 messages