Actors revamp phishing campaign materials to victim more government contractors with Microsoft 365
3 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

A group of malicious actors has leveled up their phishing campaigns in order to fool huge companies (particularly those in the energy, professional services, and construction sectors) into submitting their Microsoft Office 365 account credentials. According to a report from phishing detection and response solutions company Cofense, the campaign operators made improvements in the process and design of their lure elements and are now disguising themselves as other US government agencies, such as the Departments of Transportation, Commerce, and Labor.
“Threat actors are running a series of campaigns spoofing several departments of the United States government,” said Cofense. “The emails claim to request bids for government projects but lead victims to credential phishing pages instead. These campaigns have been ongoing since at least mid-2019 and were first covered in our Flash Alert in July 2019. These advanced campaigns are well crafted, have been seen in environments protected by secure email gateways (SEGs), are very convincing, and appear to be targeted. They have evolved over time by improving the email contents, the PDF contents, and the appearance and behavior of the credential phishing pages.”
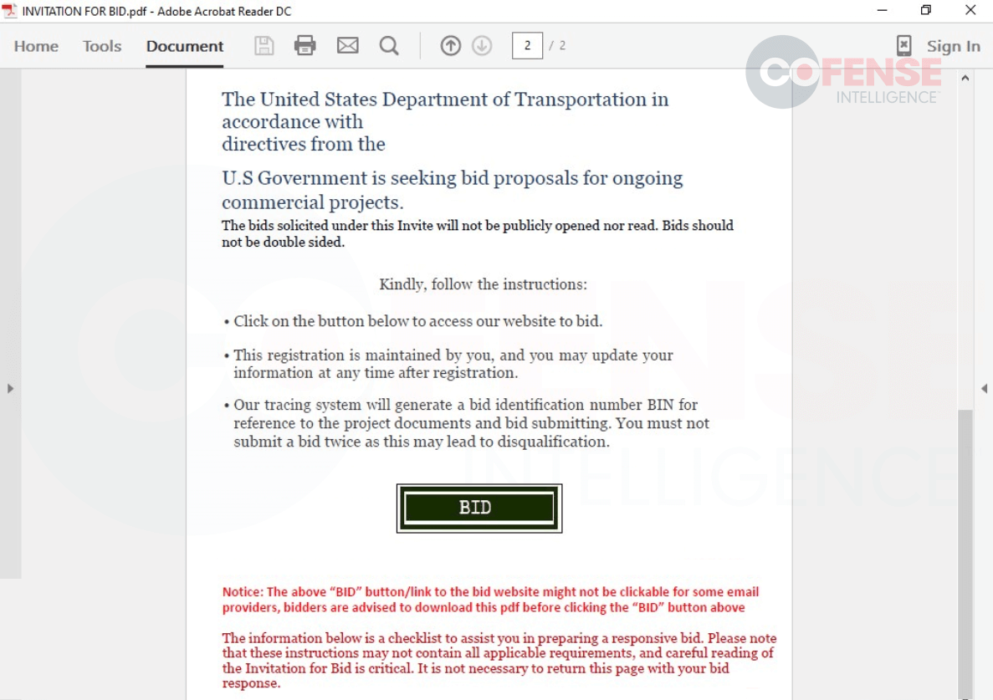
Cofense showed a series of screenshots comparing the previous and the present materials being used by the attackers. First to get these improvements are the emails and PDFs, which are now being customized to appear more authentic. “Early emails had more simplistic email bodies without logos and with relatively straightforward language,” added Cofense. “The more recent emails made use of logos, signature blocks, consistent formatting, and more detailed instructions. Recent emails also include links to access the PDFs rather than directly attaching them.”
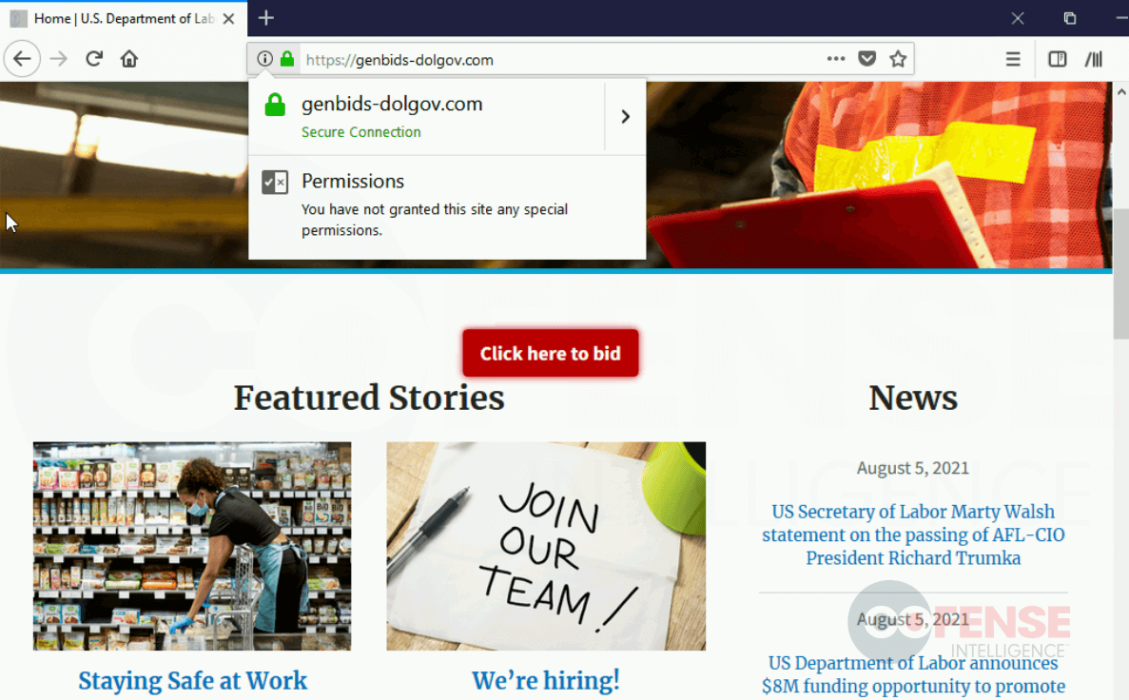
On the other hand, to prevent the suspicions of victims, the threat actors also made changes to the credential phishing page, from the login process to the design and themes. The URLs of the pages are also intendedly changed to longer ones (e.g., transportation[.]gov[.]bidprocure[.]secure[.]akjackpot[.]com), so targets will only see the .gov part in smaller browser windows. Additionally, the campaign now features captcha requirements and other instructions to make the process more believable.
The refinements in such campaigns make distinguishing real websites and documents from spoofed ones more challenging for targets, especially now that the actors are using updated information copied from original sources. Nonetheless, Cofense stressed that there are still ways to prevent falling victim to these acts. Aside from spotting small details (e.g., wrong date on pages and suspicious URLs), all recipients must always be cautious in clicking links, not just those embedded in emails but also those on attachments.