Even the police have difficulty hacking Windows Phones
1 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
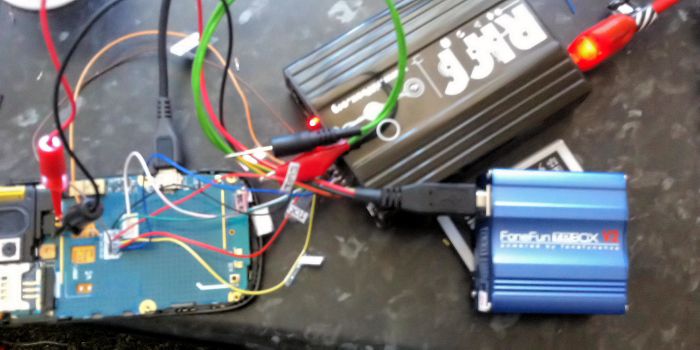
Magnet Forensics have posted an interesting article on forensic analysis of Windows Phones, showing what authorities are capable off with a recovered handset.
Interestingly it seems Windows Phones are somewhat more difficult to extract information from than other devices, with Magnet saying:
One of the major challenges for Windows Phone analysis is the acquisition phase. Unlike other devices, such as iOS and Android, JTAG and Chip-off acquisitions are the only methods to acquire most Windows Phones. This means that your traditional forensic acquisition tools such as Cellebrite, XRY, MPE+, etc., cannot acquire the data from a Windows Phone.
Examiners must manually connect to the Standard Test Access Ports (TAP) and transfer the raw physical data from memory, or manually de-solder the physical chip from the phone and read the data directly to acquire any evidence from the phone.
Sounds somewhat less trivial than simply plugging the handset in.
Magnet Forensic’s software is able to recover SMS messages, call logs and contact, and also data from 3rd party apps, but interestingly are not able to read your email. We wonder how successful the app will be against a device will full encryption.
Read more about their software here.








User forum
0 messages