Microsoft explains changes made to Edge to address Spectre vulnerability
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
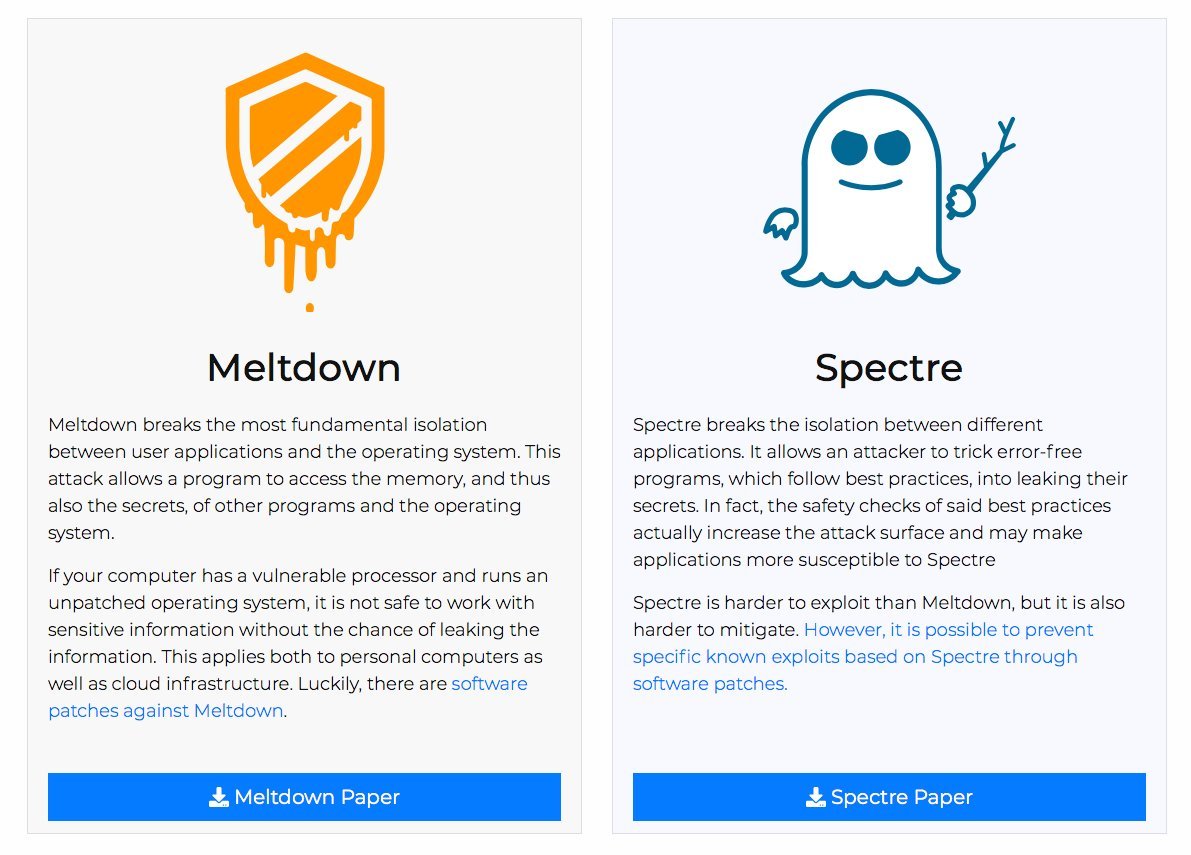

In a blog post, Microsoft has explained the changes they made to address in security updates (KB4056890) for supported versions of Edge and Internet Explorer to address the new class of “side-channel attacks.”
The first is the removal of SharedArrayBuffer from Microsoft Edge (originally introduced in the Windows 10 Fall Creators Update). SharedArrayBuffer is a generic binary data buffer that can be used to generate a view on shared memory, which lets different web workers communicate more efficiently and with greater performance, and we assume misuse of this feature lets malicious Javascript applications view parts of memory they are not meant to have access to.
The second is to reduce the resolution of performance.now() in Microsoft Edge and Internet Explorer from 5 microseconds to 20 microseconds, with variable jitter of up to an additional 20 microseconds. Performance.now() gives processes sub-millisecond precision and the changes reduce the risk of a successful exploit via Javascript as the attack relies on precise timing.
While the changes are mitigation, they are not a complete solution, and Microsoft says they plan to introduce additional mitigations as needed in future releases and may bring SharedArrayBuffer back when its safe to do so.
Read more of our coverage of the vulnerabilities and Microsoft’s response here.