Your Microsoft Exchange could be in danger if you don't properly configure DMARC settings
Microsoft updated how it handles DMARC in Exchange last year.
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
Key notes
- Microsoft Exchange is a popular tool to manage email and collab apps for businesses.
- But, a recent report finds that misconfigurations in DMAR policies increase vulnerability to email spoofing.
- Many users have not followed DMARC instructions despite Microsoft’s recommendation since 2023.
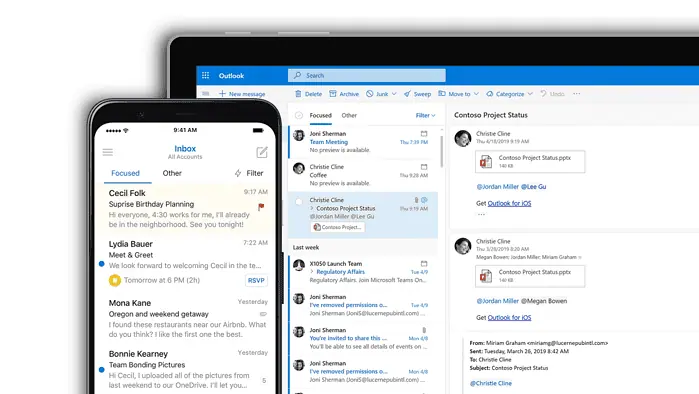
Microsoft Exchange has been one of the most popular server-based email and calendar systems around. And, unlike Microsoft Outlook which acts more of like a client-side app, Exchange gives businesses and organizations an infrastructure to manage emails, calendars, contacts, tasks, and collaboration tools.
But now, a recent report details that a misconfiguration in Exchange has left many users vulnerable to email spoofing.
Alexander Romanov of Acronis‘ Threat Research Unit says that an inadequate setup of DMAR policies, despite recommendations from Microsoft, could leave you (and third-party emails) vulnerable to these attacks. It particularly affects hybrid setups where on-premises Exchange servers interact with Exchange Online, and environments using third-party email security solutions.
“Approximately 36% of all data breaches in the EU and U.S. originate from phishing attacks,” says the team.
Last year, Microsoft improved the email verification system through DMARC, but not many users have followed the instructions. So, misconfigurations in hybrid setups and third-party MX servers can bypass essential security protocols like SPF, DKIM, and DMARC, increasing the risk of phishing and spoofing attacks.
That’s important, especially for sending large volumes of email as major providers like Gmail and Yahoo have strict standards. Even Microsoft does not recommend Microsoft 356 for bulk emailing.
Not too long ago, Microsoft also investigated an issue in Exchange Online where emails containing images were being incorrectly marked as malware and quarantined. This problem affected both inbound and outbound emails, including those with image signatures, and impacted many users.







User forum
0 messages