Turns out all you need to gain admin privileges on Windows 10 is to plug in a Razer mouse

Microsoft’s PrintNightmare fiasco has turned the eyes of the hacker community to the vulnerabilities exposed by installing 3rd party drivers and today hacker jonhat discovered that you can open a wide-open door in Windows 10 by simply plugging in a Razer wireless dongle.
https://twitter.com/j0nh4t/status/1429049506021138437
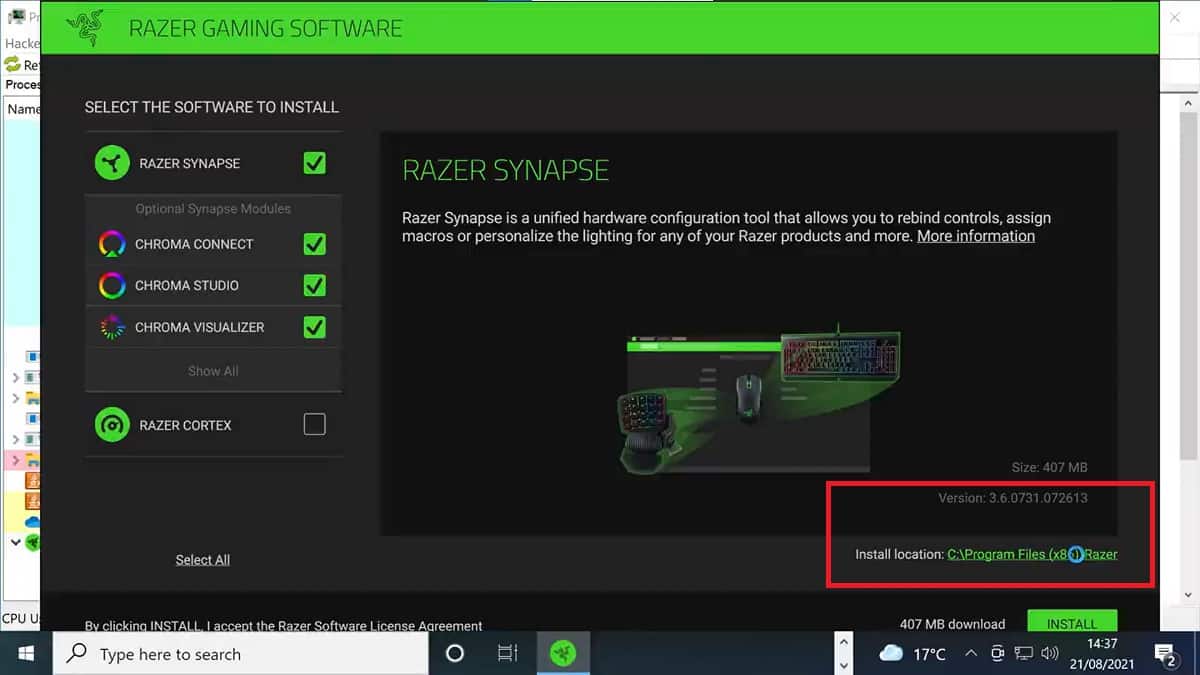
The issue is that Windows Update downloads and executes RazerInstaller as system, and that the Installer offers users the opportunity to open an Explorer window to choose where to install the drivers.
From there it only takes a shift-right-click to open a Powershell terminal with system privileges, and the hacker can basically do whatever they want.
Additionally, if the user goes through the installation process and defines the save directory to a user-controllable path like Desktop, the Installer saves a service binary there which can be hijacked for persistence and which is executed before user login on boot.
Attackers do not even need a real Razer mouse, as the USB ID can be easily spoofed.
jonhat says he attempted to contact Razer but was unsuccessful, and has therefore released the vulnerability. We assume Microsoft will move somewhat faster and remove the driver from Windows Update soon, though there is no guarantee as it would leave Razer hardware users without an easy way to access the driver.
See the video in full quality below. The attack is of course simpler than it looks, as much of the video is showing watchers that the user is indeed a standard user and that Windows is fully patched:
https://streamable.com/q2dsji
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more



User forum
0 messages