New Zero-day Double Kill malware in the wild, spreads via infected Office documents
1 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
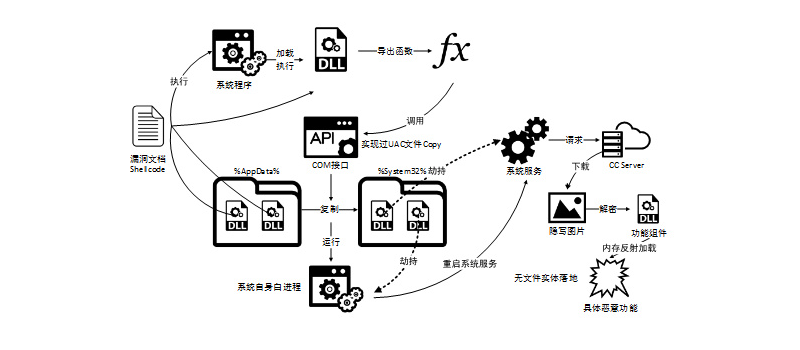
Chinese security company Qihoo 360 has discovered a new form of malware currently in the wild which is actively exploiting a zero-day flaw in Internet Explorer to install a backdoor trojan on the PC of Windows users.
Users do not need to be actively using Internet Explorer as the web page comes embedded in the infected Office document.
Qihoo 360 notes that after the user opens the document, all exploit code and malicious payload are loaded through the remote server. The late exploit phase of the attack uses a public UAC bypass technique and uses file steganography and memory reflection loading to avoid traffic monitoring and fileless loading.
Microsoft has been notified of the issue and Qihoo 360 recommends users not open Office documents from unknown sources and in particular to use security software, as no patch is available yet.
Via Winfuture.de