New FARGO ransomware distribution targets vulnerable Microsoft SQL servers
3 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

![]()
A recent report from the security analysis team of AhnLab Security Emergency Response Center (ASEC) reveals a new cybercriminal activity distributing FARGO ransomware that targets vulnerable Microsoft SQL servers.
“Along with GlobeImposter, FARGO is one of the prominent ransomware that targets vulnerable MS-SQL servers,” said ASEC. “In the past, it was also called the Mallox because it used the file extension .mallox.”
MS-SQL servers refer to Microsoft‘s relational database management system for storing and retrieving data for other software applications and internet services. With this, inflicting issues on it can mean big problems for businesses.
According to ASEC, the infection comes when the MS-SQL process downloads a .NET file through cmd.exe and powershell.exe. This file then downloads and loads additional malware, resulting in the generation and execution of a BAT file that ends specific processes and services.
“The ransomware’s behavior begins by being injected into AppLaunch.exe, a normal Windows program,” ASEC explained. “It attempts to delete a registry key on a certain path, and executes the recovery deactivation command, and closes certain processes.”
The researchers say the ransomware encrypts files but excludes some of them, including paths and extensions, to make the system partly accessible. “The characteristic aspect is that it does not infect files with a file extension associated with Globeimposter and this exclusion list does not only include the same type of extensions of .FARGO .FARGO2 and .FARGO3 but also includes .FARGO4, which is thought to be a future version of the ransomware,” ASEC added.
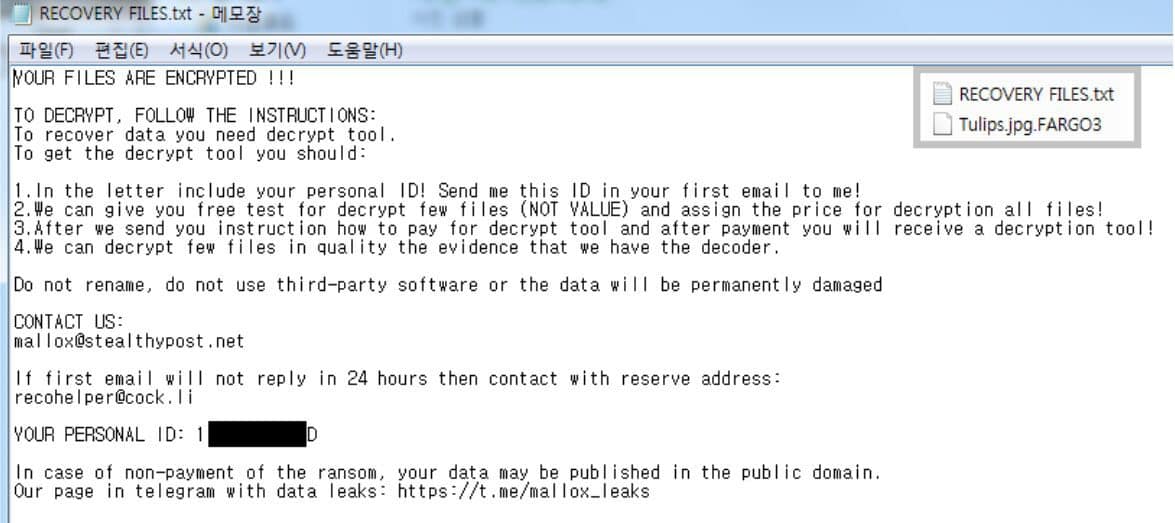
After this, the cybercriminals will rename the encrypted files using the .Fargo3 extension (e.g., OriginalFileName.FileExtension.Fargo3), while the ransom note generated by the malware will appear using the file name “RECOVERY FILES.txt.” In the message, the victims will see threats of getting their system’s file permanently deleted if they use third-party software to resolve it on their own. Additionally, cybercriminals say they would publish the data in the public domain if the victims refuse to pay the ransom.
Aside from unpatched vulnerabilities, ASEC explained that database servers like MS-SQL and MySQL servers are often the targets of brute force attacks and dictionary attacks due to weak account credentials. With this, the analysis team said that it could be prevented by simply addressing the issues and applying extra caution in protecting passwords. “Administrators of MS-SQL servers should use passwords that are difficult to guess for their accounts and change them periodically to protect the database server from brute force attacks and dictionary attacks, and update to the latest patch to prevent vulnerability attacks,” ASEC suggested.









User forum
0 messages