Microsoft release Sysmon 13 for Windows 10 with malware process tampering detection
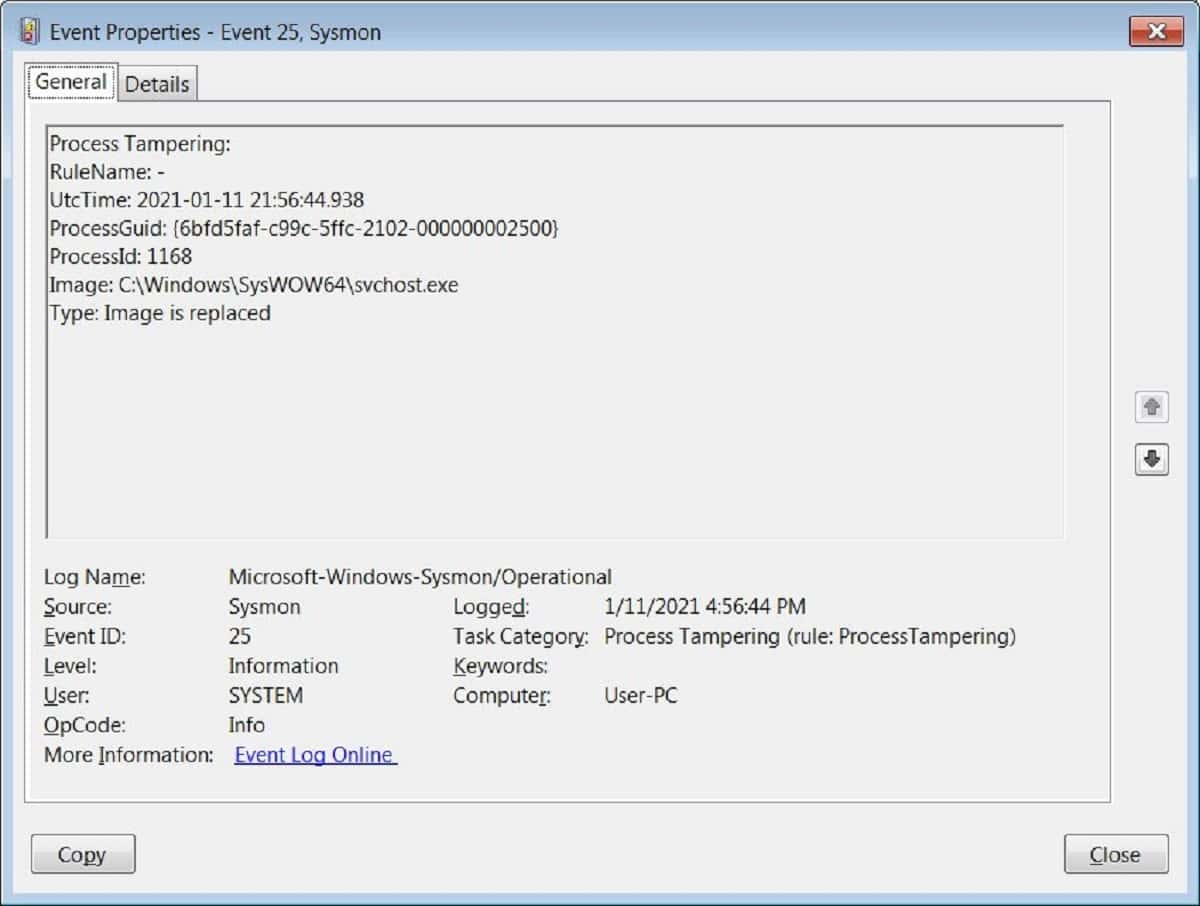
Microsoft has released a new version of the Windows 10 Sysinternals tool Sysmon, which now features the ability to detect when hackers inject malicious code into a legitimate Windows process to bypass security measures.
Sysmon 13, which lets you monitor the activity of Windows 10 processes, can now detect process hollowing or process herpaderping techniques which would normally not be visible in Task Manager.
Process hollowing is when malware launches a legitimate process in a suspended state and replaces legitimate code in the process with malicious code. This malicious code is then executed by the process, with whatever permissions are assigned to the process.
Process herpaderping is where malware modifies its image on the disk to look like legitimate software after the malware is loaded. When security software scans the on-disk file, it will see a harmless file while the malicious code runs in memory.
The technique is in active use by known malware including Mailto/defray777 ransomware, TrickBot, and BazarBackdoor.
To enable process tampering detection, admins need to add the ‘ProcessTampering’ configuration option to a configuration file. You read the documentation on Sysinternals’ site here.
It is notable that BleepingComputer found false positives with Chrome, Opera, Firefox, Fiddler, Microsoft Edge and various setup programs.
You can download Sysmon from the dedicated Sysinternal’s page or https://live.sysinternals.com/sysmon.exe.
via BleepingComputer
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more



User forum
0 messages