Integration of Lookout Mobile Endpoint Security with Microsoft EMS now generally available
3 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
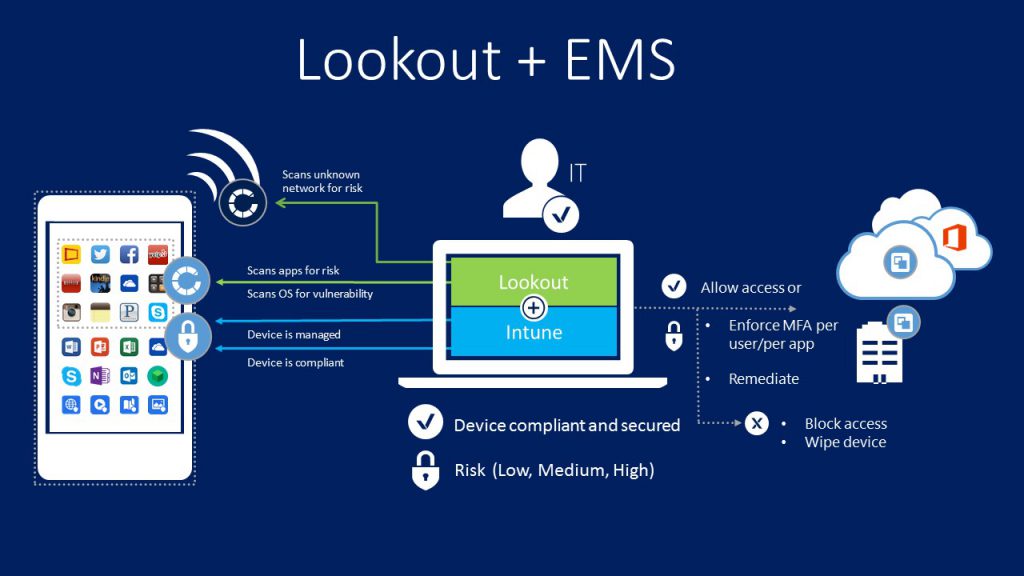
Back in June, Lookout announced their partnership with Microsoft that will integrate Lookout Mobile Threat Protection with the Microsoft Enterprise Mobility + Security suite. The integration between Lookout and Microsoft EMS helps an enterprise to benefit from mobile productivity with the assurance that their corporate data are better protected. Today, Lookout announced the general availability of its integration of Lookout Mobile Endpoint Security with Microsoft Enterprise Mobility + Security (EMS).
Lookout protects against threats across three attack vectors:
- App-based threats: Trojans, spyware, rootkits, as well as non-compliant apps that leak sensitive data
- Network-based threats: man-in-the-middle and SSL attacks that can steal encrypted data-in-transit
- OS-based threats: Advanced jailbreaking of iOS devices and rooting of Android devices
Conditional access policies within Microsoft EMS allows an enterprise to protect corporate data from unauthorized access based on customizable factors, such as location, device and user state, application sensitivity and risk. With Lookout and EMS integrated solution, if a device is determined to be non-compliant due to a mobile risk identified by Lookout, access to data like Microsoft Office 365 can be blocked using Microsoft EMS conditional access policies. When access is blocked, end users are provided a walkthrough by Lookout to help resolve the issue and regain access to company resources.
Here’s How the Integration Works:
- Allow access from devices to corporate e-mail only if the risk score is “Secured” or “Low.”
- Not synchronize corporate files to a device if its risk score is “High.”
- Not allow access to any corporate assets if Lookout’s app is not running on the device and/or properly reporting device health. It will then automatically guide users to download and activate Lookout’s app.
- Enforce a policy to deny access for a specific group of business critical apps when devices are not compliant to Lookout. General purpose LoB apps, however, would not be restricted.
- Selectively allow access to a primary collection of apps regardless of risk, while restricting access to a secondary list of apps when risk score is “Secured” or “Low.”
- Receive alerts when “High” risk devices are detected in their environments.
- Automatically trigger Lookout’s self-remediation flow when devices are non-compliant or “High” risk to them block from accessing corporate resources.
- Retire or wipe a device when it becomes “High” risk.
- The service integration here is seamless to our enterprise customers leveraging the assets of EMS to enable unified device and user (both end-user and IT Professional) identity through Azure Active Directory.
Microsoft today confirmed that they are already a deployed customer of Lookout and they use Lookout in conjunction with EMS on the iOS and Android devices. Also, Microsoft confirmed that they have made an investment in Lookout. The investment amount is not disclosed yet.








User forum
0 messages