Hackers are using old Microsoft Office vulnerabilities to Distribute FELIXROOT and steal files
2 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more


A new malware has emerged and it’s using the olf Microsft Office vulnerabilities to access and steal data. Dubbed Felixroot, the malware is delivered to individuals in Ukraine using a weaponised phishing email claiming to contain seminar information on environmental protection.
The backdoor was discovered back in 2017 but went silent for a few months. The new exploit was identified by researchers at FireEye who made the connection back to the old malware used in Ukraine last year. The malware exploits two of the Microsoft Office vulnerabilities namely, CVE-2017-0199 and CVE-2017-11882. The malware is distributed using a file named “Seminar.rtf”.
Once in, the file drops an embedded binary file into %temp% which is used to execute the FELIXROOT dropper. The dropper will then create two files, an LNK file that points to %system32%\rundll32.exe, and the FELIXROOT loader component. The LNK file will then execute the loader component of FELIXROOT and the backdoor component which is completely encrypted using custom encryption that uses XOR with a 4-byte key. Once installed into the memory, it will sleep for 10 minutes before looking for the command to be launched and connecting with the C&C server, which stolen data is secretly sent to. According to FireEye, the malware uses the Windows API to get the computer name, username, volume serial number, Windows version, processor architecture and two additional values.
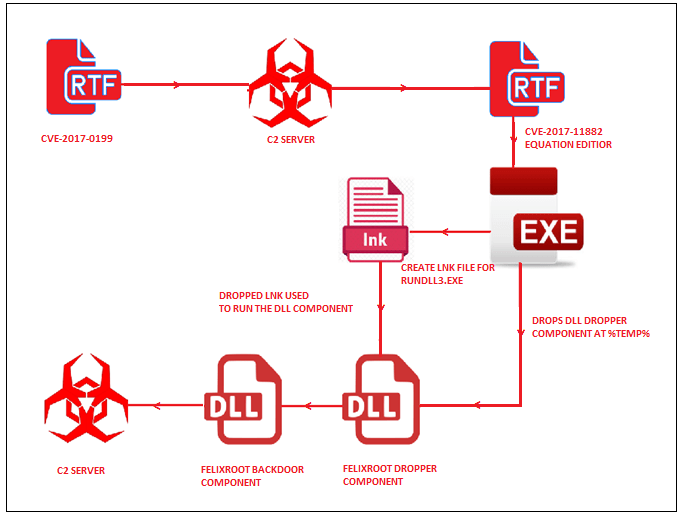
Once the data is stolen, FELIXROOT stops the execution and wipes off the digital footprint from the victim’s computer. The malware is designed to make sure no one can trace it back to the group behind it. FireEye said that they’re still working on the malware and since it’s an ongoing investigation, FireEye hasn’t revealed any specifics yet.
However, the good news is, Microsoft has rolled out patches last year so the best way to protect data is to keep everything up-to-date. Unfortunately, the organizations don’t usually apply patches on time which is allowing the malware to work and even spread. Microsoft has warned everyone several times about the dangers of not keeping everything updated. That said, very few actually download and install security updates on time and companies are usually late to apply patches which results in hacks or malware attacks.
Via: GB Hackers









User forum
0 messages