Excel is being used as fresh bait for phishers- here's how.
2 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
Evil Corp has found a new way to phish their victims- using Microsoft Excel documents.
The cybercrime group, also known as TA505 and SectorJo4, are financially motivated cybercriminals. They’re renowned for targeting retail companies and financial institutions with large-sized malicious spam campaigns, using Necurs botnet; but now, they’ve adopted a new technique.
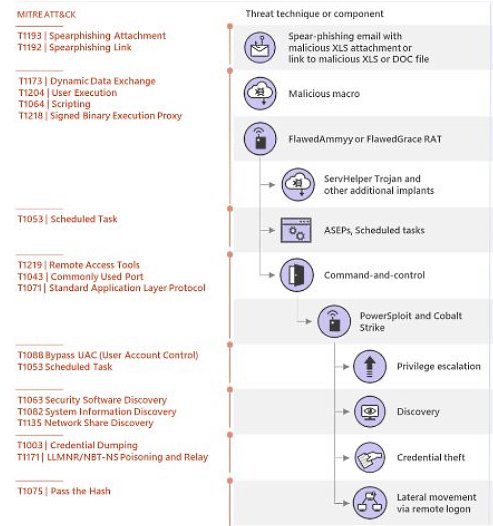
In their latest scam, they’re sending attachments featuring HTML redirectors with malicious Excel documents. Through the links, they’re distributing remote access Trojans (RATs), as well as the malware downloaders that delivered the Dridex and Trick banking Trojans. This also includes Locky, BitPaymer, Philadelphia, GlobeImposter, Jaff ransomware strains.
“The new campaign uses HTML redirectors attached to emails. When opened, the HTML leads to the download Dudear, a malicious macro-laden Excel file that drops the payload,”
“In contrast, past Dudear email campaigns carried the malware as an attachment or used malicious URLs.” -Microsoft Security Intelligence’s researchers.
Dudear (aka TA505/SectorJ04/Evil Corp), used in some of the biggest malware campaigns today, is back in operations this month after a short hiatus. While we saw some changes in tactics, the revived Dudear still attempts to deploy the info-stealing Trojan GraceWire.
— Microsoft Threat Intelligence (@MsftSecIntel) January 30, 2020
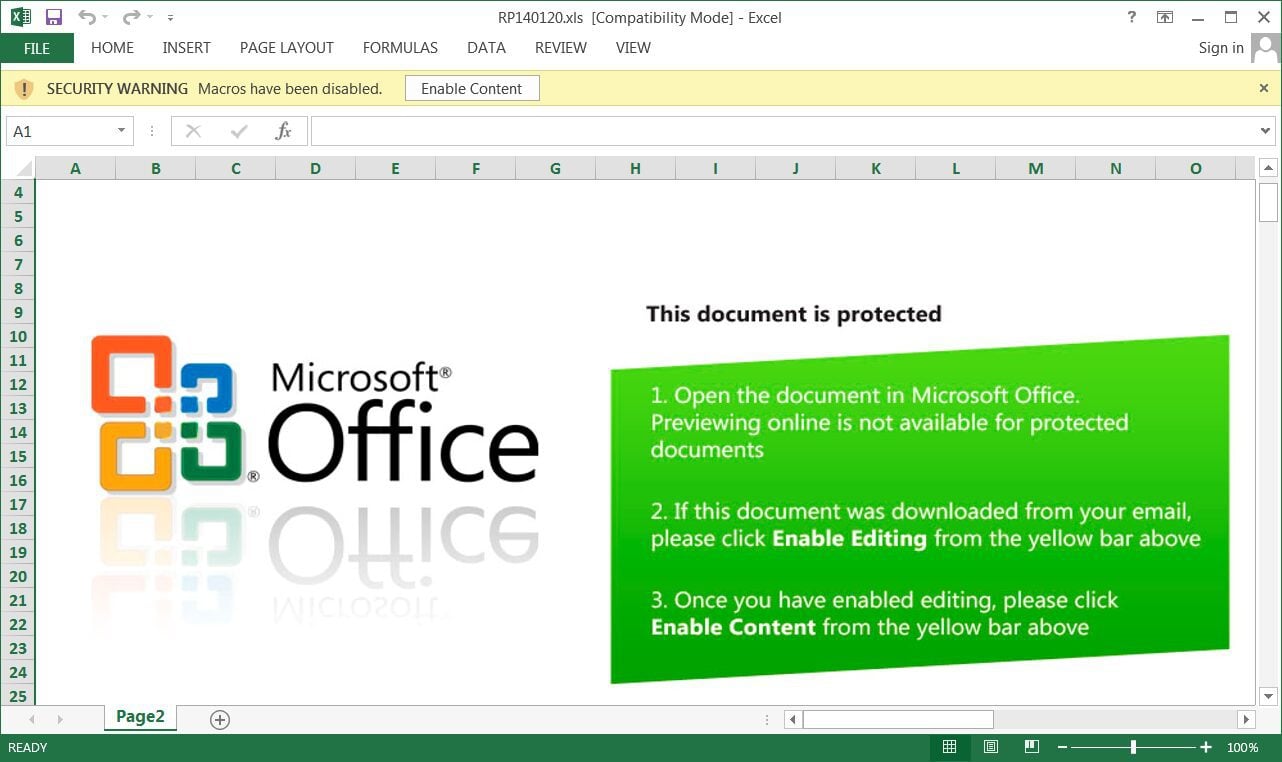
Upon opening the HTML attachment, the victim will automatically download the Excel file. Once they open it, this is what they’re met with:
Once the target clicks on “Enable Editing” as they’re instructed to in the document, they’ll unleash the malware on their system.
After this point, their device will also be infected with an IP traceback service, which “track(s) the IP addresses of machines that download the malicious Excel file.”
Threat Analytics report (Microsoft)
As well as this, the malware includes GraceWire- an info-stealing Trojan, which collects sensitive information and relays it back to the perpetrators via a command-and-control server.
View the full list of Indicators of Compromise (IOCs), including SHA-256 hashes of the malware samples used in the campaign, here and here.
Source: bleepingcomputer