Warning: Do not activate Edge, Chrome enhanced spellcheck features

If you are using the enhanced spellcheck features of Edge and Chrome, it is time to quit them as a new report shows the capability can actually send your form data to the tech giants that own the said browsers. (via Bleeping Computer)
According to the JavaScript security company named otto-js, this happens when Chrome’s Enhanced spell check feature (chrome://settings/?search=Enhanced+Spell+Check) and Edge’s Microsoft Editor Spelling & Grammar Checker browser addon are activated manually by the users. Nonetheless, note that both browsers have their own basic spellcheckers enabled by default, but they don’t pose a security risk since they don’t behave the way the enhanced features do.
When activated, the features can send data to Microsoft and Google. The information that will be transmitted depends on the form you are filling out on specific websites, which means the more info you share and fill form fields, the more data could be sent to the companies when the enhanced spellcheck features are activated. For instance, a website you are visiting might require you to provide your personally identifiable information (PII), such as your full name, home address, email address, Social Security Number, passport number, driver’s license number, credit card numbers, date of birth, and more. Worse, your passwords could also be transmitted to Microsoft and Google, according to the otto-js Research Team, calling the process “Spell-jacking” that “violates a fundamental security principle of ‘need-to-know’ and could be considered a violation of privacy.”
“If ‘show password’ is enabled, the feature even sends your password to their 3rd-party servers,” Josh Summitt, Co-Founder and CTO of otto JavaScript Security, shared the discovery while testing the company’s script behaviors detection. “While researching for data leaks in different browsers, we found a combination of features that, once enabled, will unnecessarily expose sensitive data to 3rd Parties like Google and Microsoft. What’s concerning is how easy these features are to enable and that most users will enable these features without really realizing what is happening in the background.”
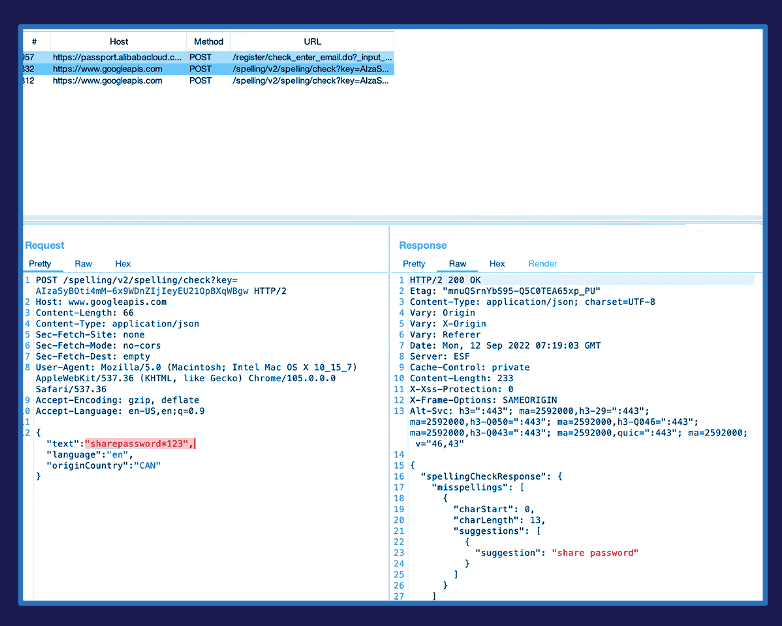
Spell-jacking can happen on all websites as long as you are using Edge and Chrome and you have their enhanced spellcheck features working. To prove it, otto-js shared how it happened when they logged into the company’s Alibaba Cloud Account using the employee credentials (specifically the password), which were later sent to Google. Further, otto-js shared a video demonstration showing how spell-jacking exposes a company’s cloud infrastructure, including servers, databases, corporate email accounts, and password managers.
“The video uses a common scenario in the workplace to illustrate how easy it is to enable the browser-enhanced spellcheck features and how an employee could expose the company without ever knowing it,” otto-js adds. “Most CISOs would be extremely alarmed to learn that their company’s administrative credentials were unwittingly shared in cleartext with a third party, even one they generally trust.”
The JavaScript security company further underlined the names of companies and services that could be affected by the issue. It includes Alibaba – Cloud Service, Office 365, and Google Cloud – Secret Manager. AWS – Secrets Manager and LastPass were originally included on the list, but otto-js said that both have “already fully mitigated the issue.”
Aside from keeping Chrome’s Enhanced spell check feature and Edge’s Microsoft Editor Spelling & Grammar Checker browser addon untouched and deactivated, otto-js said there are additional ways the spell-jacking problem could be prevented by companies through the addition of “spellcheck=false.”
“Companies can mitigate the risk of sharing their customers’ PII – by adding ‘spellcheck=false’ to all input fields, though this could create problems for users,” suggests otto-js. “Alternatively, you could add it to just the form fields with sensitive data. Companies can also remove the ability to ‘show password.’ That won’t prevent spell-jacking, but it will prevent user passwords from being sent. Companies can also use client-side security software like otto-js to monitor and control third-party scripts.”
The security firm said it is unknown if the data transmitted to Microsoft and Google are being stored or how they are managed. Microsoft still hasn’t released any comment about it, but a Google spokesperson told BleepingComputer that “Google does not attach it to any user identity and only processes it on the server temporarily.”
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more



User forum
0 messages