Microsoft details SystemContainer, a hardware based container technology built into Windows 10
4 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
Prior to Windows 8, desktop operating system security was built almost entirely from software. The problem with that approach was that if malware or an attacker gained enough privilege, could get in-between the hardware and the operating system, or they managed to tamper with the device’s firmware components, they could also find ways to hide from the platform and the rest of your security related defenses. To fix this problem, Microsoft needed device and platform trust to be rooted in immutable hardware rather than just software, which can be tampered with.
With Windows 8 certified devices, Microsoft took advantage of a hardware based root of trust with Universal Extensible Firmware Interface (UEFI) Secure Boot. Now, with Windows 10, they are taking this to the next level by making sure that this chain of trust can also be verified using the combination of hardware base security components, such as the Trusted Platform Module (TPM), and cloud based services (Device Health Attestation (DHA)) that can be used to vet and remotely attest to the device’s true integrity.
To implement this level of security in billions of devices around the world, Microsoft is working with OEMs and chip vendors like Intel. They are releasing regular firmware updates for UEFI, locking down UEFI configs, enabling UEFI memory protection (NX), running key vulnerability mitigation tools , and hardening the platform OS and SystemContainer kernels (e.g.: WSMT) from potential SMM related exploits.
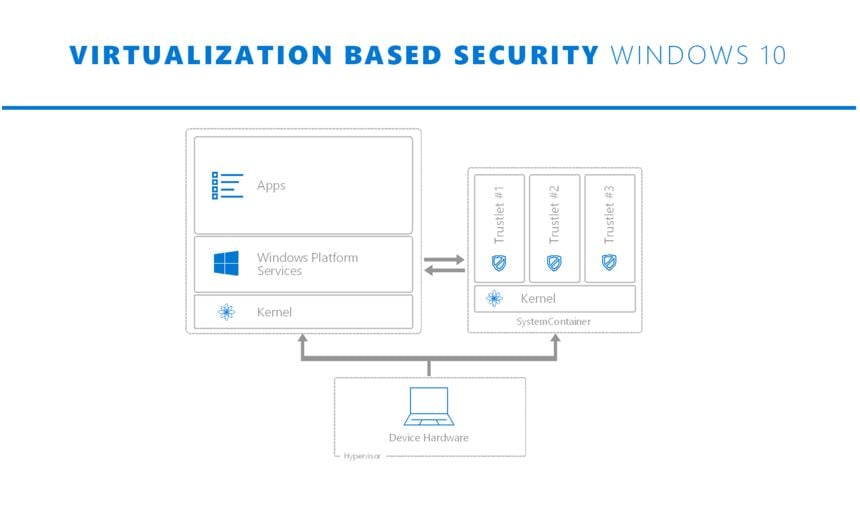
With Windows 8, Microsoft came up with the concept of modern apps (now UWP apps) which runs only inside AppContainer and, the user literally gives the app access to resources, like a document, on demand. In the case of Win32 apps, once you open the app, it can do anything that the user has the privileges to do (e.g.: open any file; change system configuration). Since AppContainers are only for UWP apps, Win32 apps remained a challenge. With Windows 10, Microsoft is bringing a new hardware based container technology that we call a SystemContainer. It is similar to an AppContainer, isolates what is running within it from the rest of the system and data. The main difference is that SystemContainer is designed to protect the most sensitive parts of the system – like those the manage user credentials or provide defenses to Windows – away from everything, including the operating system itself, which we have to assume will get compromised.
The SystemContainer uses hardware based isolation and Windows 10’s Virtualization Based Security (VBS) capability to isolate the processes running with it from everything else on the system. VBS uses the virtualization extensions on the system’s processor (e.g.: Intel’s VT-X) to isolate the addressable memory spaces between what is effectively two operating system running in parallel on top of Hyper-V. Operating system one is the one you have always known and use, and operating system two is the SystemContainer, which acts as secure execution environment that runs silently behinds the scenes. Because of the SystemContainer’s use of Hyper-V and the fact that it has no network, user experience, shared memory, or storage, the environment is well secured against attacks. In fact, even if the Windows operating system is fully compromised at the kernel level (which would give an attacker the highest level of privilege), the processes and data within the SystemContainer can still remain secure.
Services and data within the SystemContainer are dramatically less likely to be compromised, as the attack surface for these components has been significantly reduced. SystemContainer powers security features including Credential, Device Guard, Virtual Trusted Platform Module (vTPM). Microsoft is now adding Windows Hello’s biometrics validation components and the user’s biometric data into SystemContainer with the Anniversary Update to keep it secure. Microsoft also mentioned that they will continue to move some of the most sensitive Windows system services into the SystemContainer.