A Microsoft Teams social engineering attack happened recently on the platform
3 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
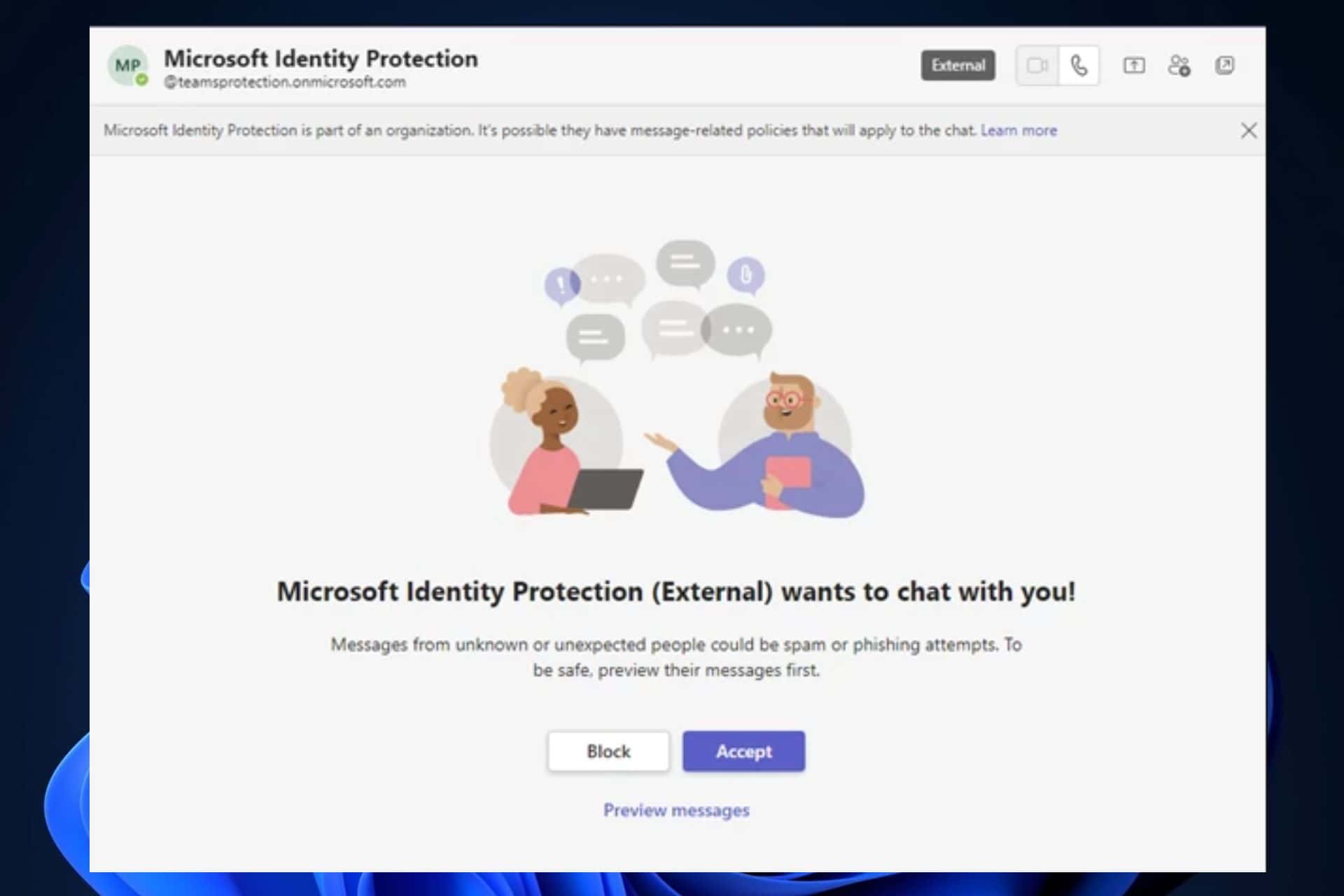
A Microsoft Teams social engineering attack was conducted by the Russian threat actor Midnight Blizzard recently. The threat actor used previously compromised Microsoft 365 tenants to create new domains that appear as technical support entities. Under these disguises, Midnight Blizzard then used Teams messages to attempt to steal credentials from organizations by engaging a user and eliciting approval of multifactor authentication (MFA) prompts.
All organizations using Microsoft Teams are encouraged to reinforce security practices and treat any authentication requests not initiated by the user as malicious.
According to their latest investigation, approximately fewer than 40 global organizations were affected by the Microsoft Teams social engineering attack. As with previous attacks from these threat actors, the organizations were mainly government, non-government organizations (NGOs), IT services, technology, discrete manufacturing, and media sectors. This makes sense, given that Midnight Blizzard is a Russian-threat actor, previously attributed by the US and UK governments as the Foreign Intelligence Service of the Russian Federation.
The attacks happened in May 2023. If you remember, another threat actor, Storm-0558, caused some serious damage to Microsoft’s servers around that time as well.
Midnight Blizzard, however, uses real Microsoft Teams credentials from compromised accounts to try to convince users to enter the code into the prompt on their device. They do so by masquerading as a technical support or security team.
According to Microsoft, Midnight Blizzard does so in 3 steps:
- The target user may receive a Microsoft Teams message request from an external user posing as a technical support or security team.
- If the target user accepts the message request, the user then receives a Microsoft Teams message from the attacker attempting to convince them to enter a code into the Microsoft Authenticator app on their mobile device.
- If the targeted user accepts the message request and enters the code into the Microsoft Authenticator app, the threat actor is granted a token to authenticate as the targeted user. The actor gains access to the user’s Microsoft 365 account, having completed the authentication flow.
Microsoft released a list of the email names that you should be careful about:
Indicators of compromise
| Indicator | Type | Description |
| msftprotection.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
| identityVerification.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
| accountsVerification.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
| azuresecuritycenter.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
| teamsprotection.onmicrosoft[.]com | Domain name | Malicious actor-controlled subdomain |
However, you can protect yourself and your organization from the Microsoft Teams social engineering attacks by following these recommendations:
- Pilot and start deploying phishing-resistant authentication methods for users.
- Implement Conditional Access authentication strength to require phishing-resistant authentication for employees and external users for critical apps.
- Specify trusted Microsoft 365 organizations to define which external domains are allowed or blocked to chat and meet.
- Keep Microsoft 365 auditing enabled so that audit records could be investigated if required.
- Understand and select the best access settings for external collaboration for your organization.
- Allow only known devices that adhere to Microsoft’s recommended security baselines.
- Educate users about social engineering and credential phishing attacks, including refraining from entering MFA codes sent via any form of unsolicited message.
- Educate Microsoft Teams users to verify ‘External’ tagging on communication attempts from external entities, be cautious about what they share, and, and never share their account information or authorize sign-in requests over chat.
- Educate users to review sign-in activity and mark suspicious sign-in attempts as “This wasn’t me”.
- Implement Conditional Access App Control in Microsoft Defender for Cloud Apps for users connecting from unmanaged devices.
What do you think about these Microsoft Teams social engineering attacks? Let us know in the comments below!








User forum
0 messages