This Microsoft Teams malware is exposing users through federated chat
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
A new Microsoft Teams malware was discovered by a group of researchers from JUMPSEC’s Red Team, and it’s been exposing users to vulnerability for quite some time.
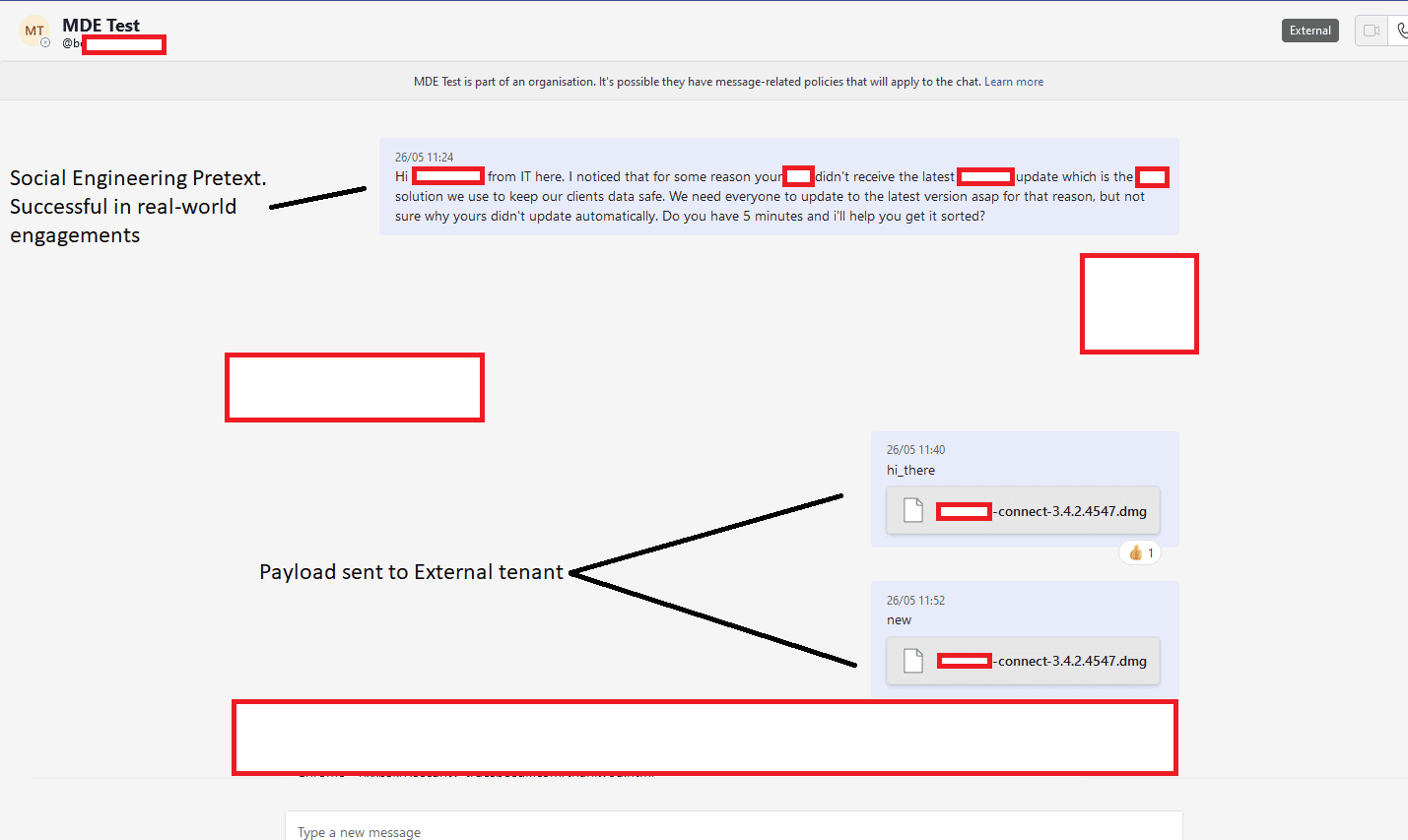
Security researchers Max Corbridge and Tom Ellson have uncovered a critical vulnerability in the latest iteration of Microsoft Teams, which exists in the External Access feature within the app.
This vulnerability poses a significant risk as it enables the potential introduction of malware into organizations utilizing Microsoft Teams in its default setup. It also allows malicious actors to deliver malware directly to staff within the organization by avoiding client-side security controls designed to block external tenants from sending files.
The functionality enables users to engage in chat and video calls with individuals external to their organization using Microsoft Teams. However, in this particular instance, it can be exploited to introduce malware into files transmitted through the inbox.
“So far, this is nothing new. However, having leveraged this social engineering avenue in the past I began wondering if this security control could be bypassed to allow for seamless delivery of payloads directly into a target’s inbox on our red team engagements,” the report reads.
“I raised this with JUMPSEC’s Head of Offensive Security (Tom Ellson) and no more than 10 minutes later we had bypassed the security control and were able to send files into a target organisation,” it continues.
As the report entails, this vulnerability presents a potentially lucrative opportunity for threat actors to deliver malicious payloads, as it bypasses many modern anti-phishing security controls. The ease of buying a domain similar to the target organization and registering it with M365 eliminates the need for extensive infrastructure setup typically required for convincing phishing campaigns.
By utilizing a trusted Sharepoint domain, the payload is served as a file within a target’s Teams inbox, leveraging the reputation of Sharepoint and reducing the likelihood of detection by staff trained to avoid clicking on email links.