Microsoft rolls out new Microsoft Authenticator features for enterprise users
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
Microsoft has announced new capabilities for Microsoft Authenticator for corporate users intended to make it even more secure and easier to rollout for our admins.
The new features include:
- Admins can now prevent accidental approvals in Microsoft Authenticator with number matching and additional context (Public Preview).
- Admins can now setup GPS-location based Conditional Access policies using Microsoft Authenticator (GA).
- Admins can now nudge their users to setup Microsoft Authenticator during sign-in using the Registration Campaign feature (GA).
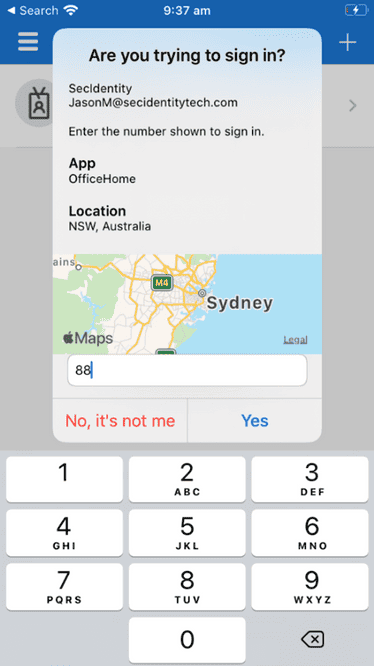
Number matching in Microsoft Authenticator MFA experience (Public Preview)
To increase security and reduce accidental approvals, admins can require users to enter the number displayed on the sign-in screen when approving an MFA request in Authenticator.
To learn how to enable number matching, click here.
Additional context in Microsoft Authenticator approval requests (Public Preview)
Another way to reduce accidental approvals is to show users additional context in Authenticator notifications. This feature will show users which application they are signing into and their sign-in location based on IP address.
To learn how to enable additional context click here.
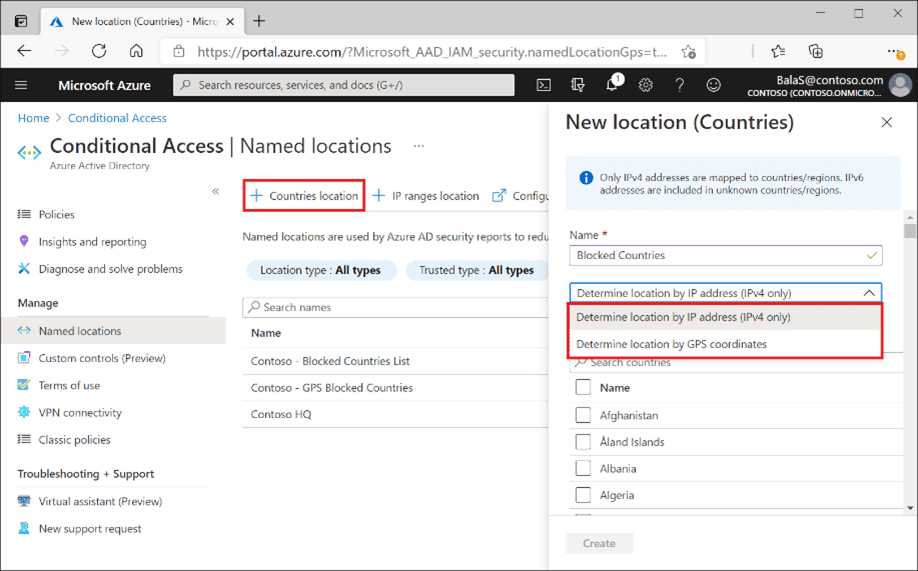
GPS-based Named Locations (Generally Available)
Admins can now use Conditional Access policies to restrict resource access to the boundaries of a specific country by using the GPS signal from the Microsoft Authenticator.
Users with this feature enabled will be prompted to share their GPS location via the Microsoft Authenticator app during sign-in. To ensure the integrity of the GPS location, Microsoft Authenticator will deny authentication if the device is jailbroken or rooted.
To learn more, check out admin documentation, Graph API documentation, and FAQ page.
Microsoft Authenticator Registration Campaign (Generally Available)
Using the Microsoft Authenticator Registration Campaign, you can now nudge users to set up Authenticator and move away from less secure telephony methods. The feature targets users who are enabled for Microsoft Authenticator but have not set it up. Users are prompted to set up Authenticator after completing an MFA sign-in and after the set-up experience their default authentication method is changed to the Microsoft Authenticator app.
To learn how to enable a Registration Campaign, click here.
Microsoft is urging admins to try these security upgrades to Microsoft Authenticator and provide feedback at aka.ms/AzureADFeedback.








User forum
0 messages