Microsoft missed a critical vulnerability in Windows that allowed hackers to transfer admin rights to other accounts
2 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
A new report shared by Colombian cybersecurity expert Sebastian Castro, reveals shocking details about a critical vulnerability in Windows. Castro shared details about the vulnerability which would allow hackers to transfer Admin rights to other accounts.
According to CSL, the vulnerability exists since Windows XP and allows administrators’ rights to be transferred to arbitrary accounts. Castro wrote Metasploit module himself to test and demonstrate the vulnerability.
So I decided to write a Metasploit module, by taking as a reference the enable_support_account post module which was developed by my colleague and friend Santiago Díaz. This module exploits the core of the vulnerability mentioned in the above reference, but it is limited to work only in XP/2003 Windows version, by modifying a security descriptors of the support_388945a0 built-in account.
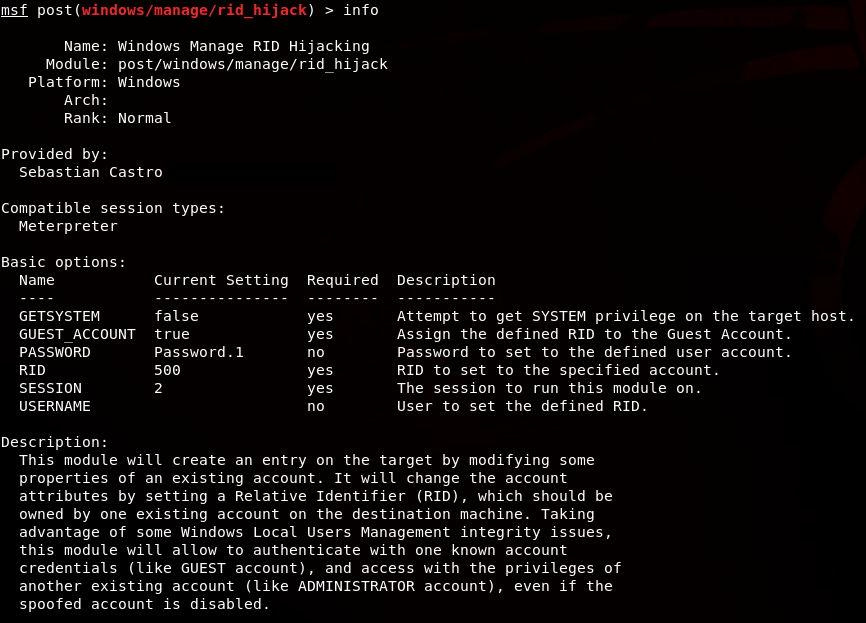
However, the rid_hijack module automatizes this attack with any existing account on the victim. It could be found in post/windows/manage/rid_hijack.
– Sebastian Castro
Once the module was set, Castro tested it on several Operating Systems including Windows XP, Windows Server 2003, Windows 8.1 and Windows 10. He also went on to explain how the whole process works and will allow hackers to transfer all the admin rights from an Administrator account to a Guest account.
Regardless of the version since XP, Windows uses the Security Account Manager (SAM) to store the security descriptors of local users and built-in accounts. As is mentioned in How Security Principals Work, every account has an assigned RID which identifies it. Different from domain controllers, Windows workstations and servers will store most part of this data in the HKLM\SAM\SAM\Domains\Account\Users key, which requires SYSTEM privileges to be accessed.
– Sebastian Castro
The unfortunate thing is that a report was sent to Microsoft around 10 months ago by the company but was never answered. This gave them permission to disclose the vulnerability after a fixed period of time. However, Günter Born, recently reported that the adaption of the baseline Group Policy Object might prevent the hack from taking place in a real-life situation. That said, we are still waiting for Microsoft to release an official statement.