Microsoft just patched 6 zero-days vulnerabilities, but you need to update your OS
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
Microsoft released a new wave of security updates for its software products, fixing 57 vulnerabilities in total. Most notably, this update addresses six zero-day vulnerabilities that have been actively exploited.
Curiously enough, Windows 11 and Server 2019 onwards didn’t receive any patches. This means that these OSs are not vulnerable, as explained by Adam Barnett, Rapid7’s lead software engineer:
It’s not clear why newer Windows products dodged this particular bullet. The Windows 32 subsystem is still presumably alive and well, since there is no apparent mention of its demise on the Windows client OS deprecated features list.
These are the vulnerabilities you should watch out for
- CVE-2025-24985: An integer overflow and heap-based buffer overflow in the Windows Fast FAT File System Driver that could enable an attacker to execute code on a target system.
- CVE-2025-24984: A Windows NTFS remote code execution vulnerability that can be triggered with a malicious USB.
- CVE-2025-24993: A heap-based buffer overflow in Windows NTFS could be exploited by mounting a malicious virtual hard disk.
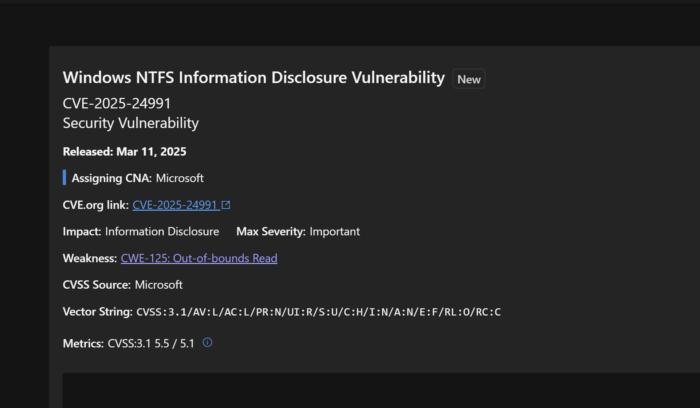
- CVE-2025-24991: An out-of-bound read vulnerability in Windows NTFS which can lead to information disclosure.
- CVE-2025-26633: A flaw in the Microsoft Management Console that does not correctly neutralize input, which malicious files can exploit.
- CVE-2025-24983: Use-after-free in Windows Win32 Kernel Subsystem that can lead to privilege escalation.
These vulnerabilities target Windows’s core elements and are, therefore, serious security threats. However, their active exploitation indicates that threat actors are already using them in attacks.
Beyond the zero-day flaws, Microsoft fixed several other significant vulnerabilities, including two that could enable remote code execution in Windows Remote Desktop Services. Over three-quarters of the addressed vulnerabilities are tagged as high-severity.
Due to the severity of these vulnerabilities and the fact that they are currently being exploited, it is recommended that users and companies apply these security patches immediately. Failure to do so could leave systems vulnerable to attack.
It is the sixth month in a row that Microsoft has fixed zero-days in its Patch Tuesday updates, further emphasizing the need to have the systems up to date.
Users are recommended to make a backup of their data before applying updates and check for issues during the update process. Checking official Microsoft links and documentation regularly will help you stay one step ahead regarding cybersecurity management.






User forum
0 messages