Microsoft delivers Hafnium patches for unsupported versions of Exchange Server
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

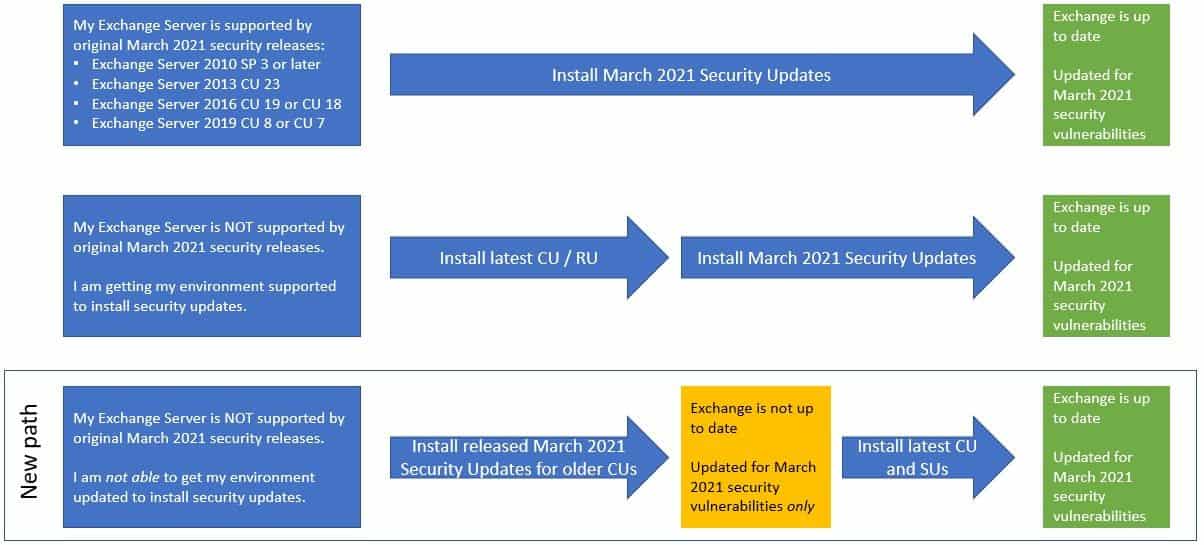
Admins who have not kept their stand-alone Exchange server up to date with patches may have difficulty applying the update Microsoft released a week ago to patch the 4 flaws in the software which is being actively exploited by the Chinese hacker group which is estimated to have compromised more than 60,000 installations so far.
Microsoft’s initial guidance was for admins to bring their servers up to date and then apply the patches, but the company recognized that this may be difficult to do in all production environments.
Microsoft has now released patches for the 4 flaws (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065) which contains no other fixes or improvements, and which are designed to be applied to un-updated installations of Exchange 2016 and 2019.
Admins can now install the updates and be protected, and then bring their servers up to date with regular Cumulative Updates at their leisure.
Microsoft notes:
- These update packages contain only fixes for March 2021 CVEs (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065); no other product updates or security fixes are included. Installing these updates does not mean an unsupported CU is now supported.
- Updates are available only through the Microsoft Download Center (not on Microsoft Update).
- We are producing updates only for some older CUs for Exchange 2016 and 2019.
- If you are running a version of Exchange not covered by these updates, consider either rolling forward to a CU package that has an applicable SU, or rolling forward to a supported CU (preferred option). In case you need to go forward with CUs, please see: best practices for installation of Exchange updates (applies to all versions of Exchange).
A reboot is required.
Read all the detail on getting the patches at Microsoft here.






User forum
0 messages