Windows hacker manages to install Google Play Store on Windows 11 WSA
2 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
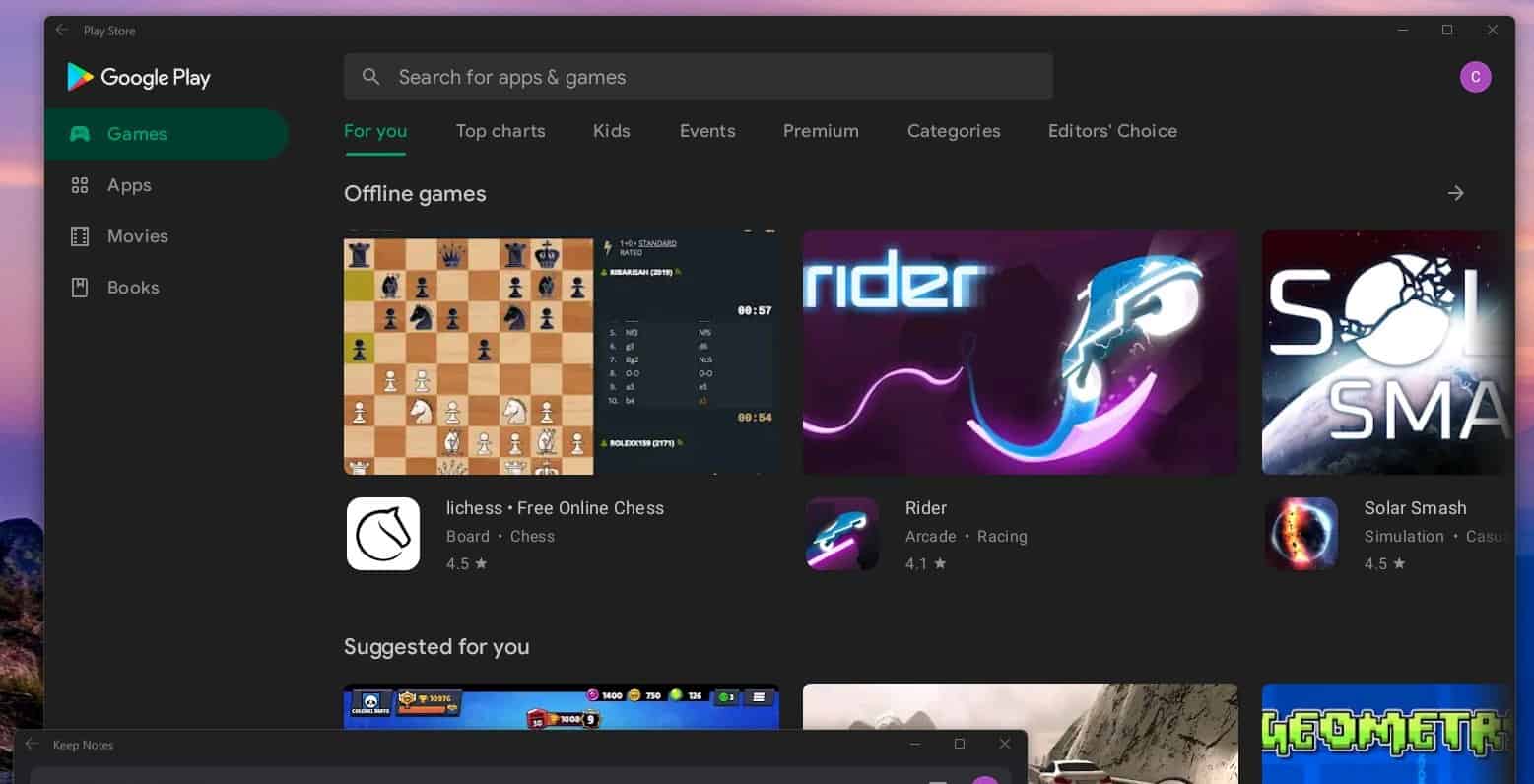
Microsoft recently released their Windows Subsystem for Android (WSA) for Windows 11 Insiders, and while it is an amazing achievement, at present it is pretty limited, with access to only about 50 titles in the Amazon app store.
While it is possible to side-load any Android app, in practice the best apps are in the Google Play Store, and those will not work on WSA as it lacks Google Play Services, needed for most apps in that store.
Of course, Windows is nothing but hackable, and it appears Windows hacker ADeltaX has cracked the problem, and managed to install Google Play Services, including the Store, on Windows 11.
— ADeltaX (@ADeltaXForce) October 22, 2021
He has left all the necessary files and instructions on GitHub but it seems for now only experts need to apply.
Currently, the instruction reads:
- Download MSIXBUNDLE (use store rg-adguard to download the msixbundle, Package id: 9P3395VX91NR)
- INSTALL WSL2 (ubuntu/debian, any other distro could work)
- INSTALL unzip lzip
- DOWNLOAD GAPPS PICO FROM OPENGAPPS (x86_64, 11, PICO)
- EXTRACT MSIXBUNDLE, EXTRACT MSIX (YOUR ARCH) TO A FOLDER, DELETE (APPXMETADATA, APPXBLOCKMAP, APPXSIGNATURE, [CONTENT_TYPES])
- COPY IMAGES (SYSTEM.IMG, SYSTEM_EXT.IMG, PRODUCT.IMG, VENDOR.IMG) TO #IMAGES
- COPY (GAPPS PICO ZIP) TO #GAPPS
- EDIT (VARIABLES.sh) AND SET ROOT FOLDER
- EXECUTE:
- extract_gapps_pico.sh
- extend_and_mount_images.sh
- apply.sh
- unmount_images.sh
- COPY IMAGES FROM (#IMAGES FOLDER) TO YOUR EXTRACTED MSIX FOLDER
- OPEN POWERSHELL (NOT CORE) AS ADMIN, EXECUTE (Add-AppxPackage -Register PATH_TO_EXTRACTED_MSIX\AppxManifest.xml)
- RUN WSA WITH GAPPS, ENJOY
WORKAROUND FOR SIGN IN ISSUE:
(ADB SHELL ROOT WITH su)
- COPY (kernel FILE) FROM (misc FOLDER) TO (Tools FOLDER) IN YOUR EXTRACTED MSIX FOLDER
- NOW YOU CAN USE su IN ADB SHELL ENTER ADB SHELL, TYPE su THEN TYPE setenforce 0 YOU CAN NOW SIGN IN
ADeltaX is however promising to rewrite the instructions soon to make them more palatable.
The achievement reminds me of Microsoft killing Android apps for Windows Phone, not because it worked too poorly, but because it worked too well.
Will our readers be trying this hack? Let us know below.
Update: There is now a video tutorial available:









User forum
0 messages