Report: Windows 10 is less secure than Windows 7 with EMET
3 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
The Enhanced Mitigation Experience Toolkit (EMET) is a tool that helps prevent vulnerabilities in software from being successfully exploited. EMET uses security mitigation technologies as special protections and obstacles that an exploit author must defeat to exploit software vulnerabilities. These security mitigation technologies do not guarantee that vulnerabilities cannot be exploited. However, they work to make exploitation as difficult as possible to perform.
Since Windows 10 includes mitigation features that EMET administrators have come to rely on such as DEP, ASLR, and Control Flow Guard (CFG) along with many new mitigations to prevent bypasses in UAC and exploits targeting the browser, Microsoft has decided to stop supporting EMET after July 31, 2018.
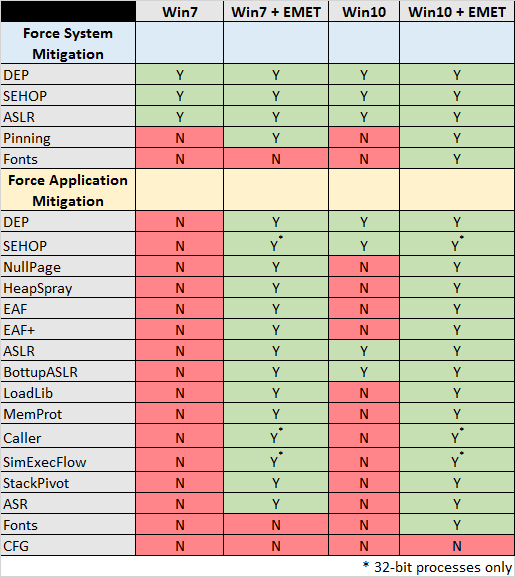
According to a report from Carnegie Mellon University security researcher, a Windows 10 device is less secure than a Windows 7 device with EMET running on it. His report claims that Windows 10 does not provide the additional protections that EMET does and EMET is still an important tool to help prevent exploitation of vulnerabilities. Check out the table below,
His defense for EMET,
Windows 10 includes all of the mitigation features that EMET administrators have come to rely on such as DEP, ASLR, and Control Flow Guard (CFG) along with many new mitigations to prevent bypasses in UAC and exploits targeting the browser.
Microsoft’s statement above overlooks the primary reason for someone to run EMET. In particular, users running EMET to protect applications that do not opt in to all of the exploit mitigations that it should. Even though the underlying Windows operating system supports a mitigation, doing so does not necessarily mean that it will be applied to an application.
Developer adoption of exploit mitigations takes place at a slower rate than we’d like to see. For example, even Microsoft does not compile all of Office 2010 with the /DYNAMICBASE flag to indicate compatibility with ASLR. What is the impact? An attacker may be able to work around ASLR by causing a non-DYNAMICBASE library to be loaded into the process space of the vulnerable application, potentially resulting in successful exploitation of a memory corruption vulnerability. What do we do to protect ourselves against this situation? We run EMET with application-specific mitigations enabled!
His final recommendations,
- From an exploit mitigation perspective, upgrading to Windows 10 is a good idea.
- Installing EMET with application-specific mitigations configured is also a good idea.
- EMET provides some protection against zero-day vulnerabilities in supported software, as well as forever-day vulnerabilities in unsupported software.
- If the use of EMET is not possible, then the system-wide mitigations of DEP and ASLR can be applied without EMET.
- Windows 10 does not provide all of the mitigation features that EMET administrators have come to rely on.
Read his full report here.