New Squidoor malware targeted at Windows & Linux can silently leverage Outlook
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

A highly sophisticated backdoor malware called “Squidoor” was found to target South American and Southeast Asian entities. Associated with suspected Chinese attackers, Squidoor exhibits very advanced stealth capabilities, offering permanent access to the targeted networks and evading security controls.
Attackers primarily exploit IIS server vulnerabilities to gain initial access. Following exploitation, they deploy several web shells that serve as persistent backdoors. The web shells share structural and obfuscation similarities, indicating a common origin.
Both Windows and Linux can be targeted
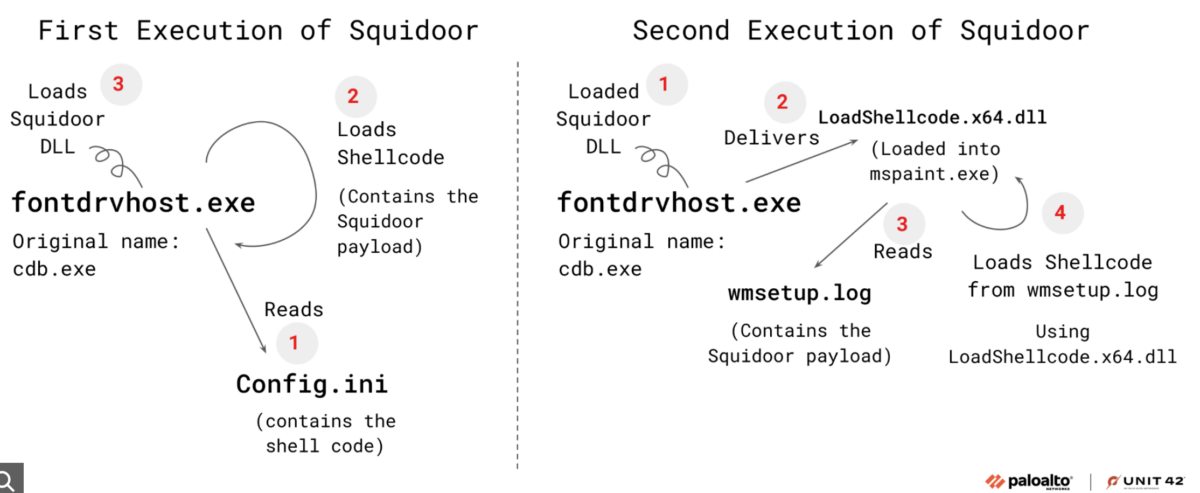
Squidoor is a cross-platform malware with Windows and Linux operating system-specific variants, expanding its coverage and attack surface. The adaptability enables the malware to infest diverse network environments, potentially impacting more targets and complicating detection and mitigation across heterogeneous infrastructures.
The malware supports multiple command and control (C2) communication protocols—ten for the Windows version and nine for the Linux version. These protocols include HTTP-based communication, reverse TCP/UDP connections, DNS tunneling, and even Microsoft Outlook mail API communication. This facilitates attackers’ easy switching between various network environments and security controls.
Outlook API exploitation
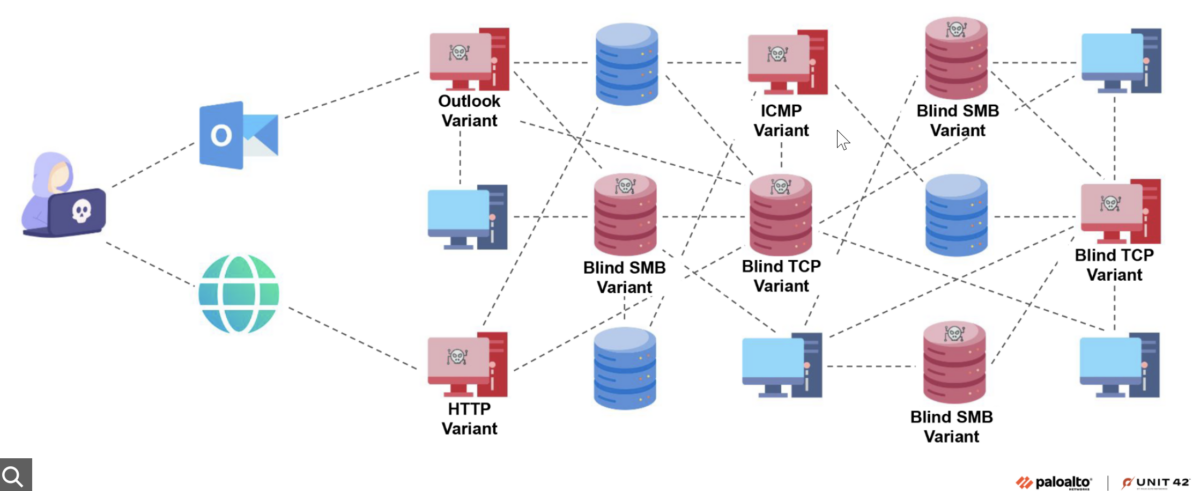
Surprisingly, Squidoor can leverage Microsoft Outlook as an undetectable communication channel. When configured for this method, the malware logs into the Microsoft identity platform using a hard-coded refresh token. The malware subsequently invokes the drafts folder within Outlook. It searches for emails with specific subject line patterns containing randomly generated numbers to distinguish different Squidoor implants. The transmission stream utilizes sophisticated encoding and encryption methods, including processing via CryptStringToBinaryA WinAPI, Base64 decoding, AES coupled with bespoke XOR decryption, and zlib decompression.
To secure persistence, Squidoor launches a timed task named “MicrosoftWindowsAppDataEPolicyManager” containing malicious shellcode that executes occasionally to maintain an open backdoor even after system reboots. The malware can also inject payloads within legitimate processes, including mspaint.exe, conhost.exe, and taskhostw.exe, to mask its activities even more.
The Squidoor attack highlights the attackers’ new tactics and the importance of tight security controls in organizations. The malware’s multi-platform capability and advanced communication features necessitate top-notch monitoring and defense systems to protect against sophisticated attacks.
Companies must periodically update and patch their systems, monitor for unusual network activity, and utilize advanced threat detection software to defend against the menace of malware like Squidoor.








User forum
0 messages