Microsoft shares COVID-19 cyber-attack threat signature data
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
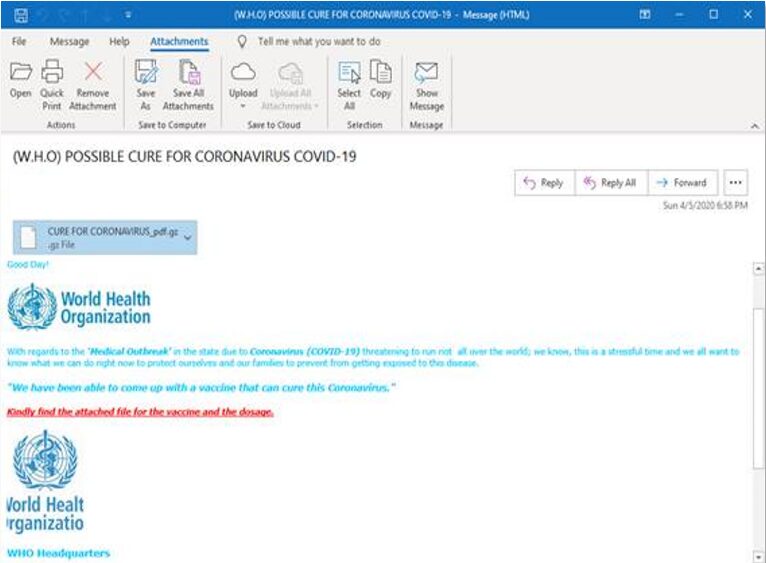
Unfortunately, the COVID-19 crisis has been used by unscrupulous actors to take advantage of business and individuals, with Microsoft frequently acting as a firewall to protect their customers from attackers.
This has resulted in Microsoft collecting trillions of signals across identities, cloud, endpoints, applications, and email, which makes it easier to identify when such an attack is in progress, and to help other security companies protect their users, Microsoft has now released this signature data as a free open source project.
“This threat intelligence is provided for use by the wider security community, as well as customers who would like to perform additional hunting, as we all defend against malicious actors seeking to exploit the COVID crisis”, noted the Microsoft Threat Intelligence Team.
The data is being made available via Azure Sentinel GitHub and the Microsoft Graph Security API and for enterprises that use MISP for storing threat data, indicators can be consumed via the MISP feed.
Microsoft is only maintaining the feed through the peak of the outbreak to help organizations focus on recovery, but says they are committed to greater transparency and taking community feedback on what types of information is most useful to defenders in protecting against COVID-related threats.
Read more at Microsoft here.
Via DarkReading




User forum
0 messages