Microsoft is working to bring extended Berkeley Packet Filter (eBPF) support to Windows
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

ZDNet reports that Microsoft is working to bring the Linux security tool extended Berkeley Packet Filter (eBPF) to Windows 10.
The tool can currently be run on Windows SubSystem for Linux, but Microsoft is working on native support, with the issue being that the tool runs code in the kernel context, which raises all kinds of security complications.
The work may be worth it, however, as eBPF is extensively used in network filtering, analysis, and management and also for system call filtering and process context tracing and forms the foundation of multiple security applications such as Cilium, Falco, and Tracee; Kubernetes observation programs like Hubble and Pixie, and toolchains such as Clang.
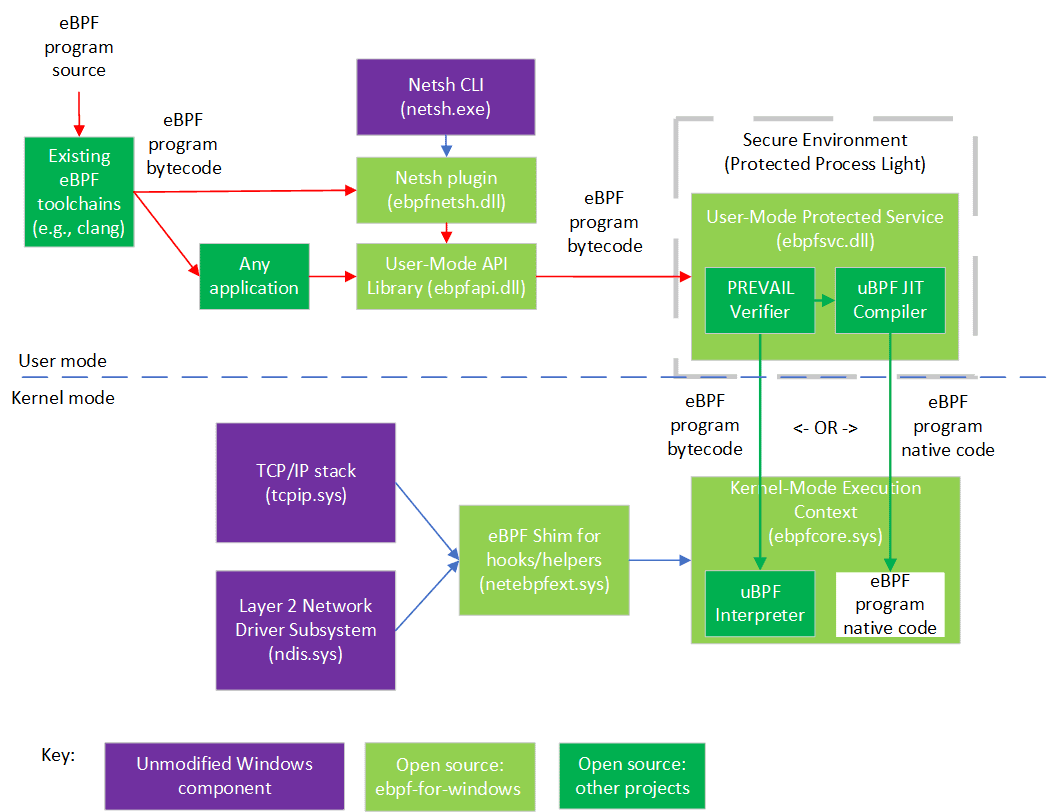
The ebpf-for-windows project aims to take several existing eBPF open-source projects and adds the “glue” to make them run on Windows.
As shown in the diagram, existing eBPF toolchains (clang, etc.) can be used to generate eBPF bytecode from source code in various languages. Bytecode can be consumed by any application, or via the Netsh command line tool, which use a shared library that exposes Libbpf APIs, though this is still in progress.
The eBPF bytecode is sent to a static verifier (the PREVAIL verifier) that is hosted in a user-mode protected process (a Windows security environment that allows a kernel component to trust a user-mode daemon signed by a key that it trusts). If the bytecode passes all the verifier checks, it can be either loaded into an interpreter (from uBPF in the kernel-mode execution context), or JIT compiled (via the uBPF JIT compiler) and have native code load into the kernel-mode execution context (but see the FAQ at bottom about HVCI).
eBPF programs installed into the kernel-mode execution context can attach to various hooks (currently two hooks so far: XDP and a socket bind hook) and call various helper APIs exposed by the eBPF shim, which internally wraps public Windows kernel APIs, allowing the use of eBPF on existing versions of Windows. More hooks and helpers will be added over time.
The end result will be a Windows-specific hosting environment for eBPF which would allow Windows developers to use open-source eBPF programs without having to recode.
Check out the ebpf-for-windows project at GitHub here.