Latest Windows 10 Zero-day Privilege Escalation bug would allow attacker to overwrite arbitrary files with data
1 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

A hacker has found another way to break the Windows 10 app security model. SandboxEscaper, who has posted 3 other zero-day bugs in Windows in the last 4 months, have published another which uses the Windows Error Reporting system to overwrite arbitrary Windows 10 files, including essential files which would not normally accessible.
SandboxEscaper posted a proof of concept for example which overwrote pci.sys, which enumerates physical device hardware, and without which PCs cannot boot.
Vulnerability analyst Will Dormann notes the hack is not reliable yet, as it relies on a race condition, so may only work in one of 100 attempts, but this may not matter if the app running the hack can check if the attack was successful, such as disabling an antivirus or other setting.
This latest 0day from SandboxEscaper requires a lot of patience to reproduce. And beyond that, it only *sometimes* overwrites the target file with data influenced by the attacker. Usually it's unrelated WER data.https://t.co/FnqMRpLy77 pic.twitter.com/jAk5hbr46a
— Will Dormann (@wdormann) December 29, 2018
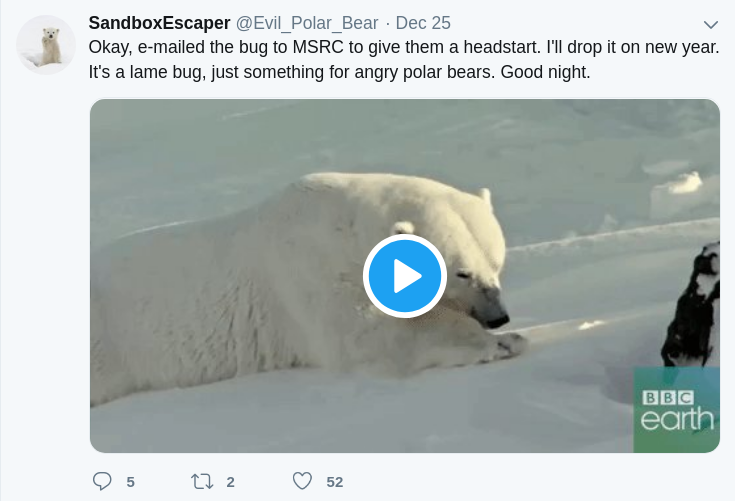
SandboxEscaper informed Microsoft a week ago on Christmas, and have now published the hack for all to see on Github, with the hope it will encourage Microsoft to rapidly fix the issue.
The exploit code can be seen at Github here.
Via BleepingComputer