There's a new Windows zero-day exploited since 2017, but Microsoft won't patch it
2 min. read
Published on

A recently disclosed zero-day vulnerability in Microsoft Windows, identified as ZDI-CAN-25373, has been actively exploited by at least 11 state-sponsored hacking groups from countries including North Korea, Iran, Russia, and China since 2017.
The flaw resides in handling Windows Shortcut or Shell Link (.LNK) files, enabling attackers to execute arbitrary code on targeted systems. By crafting malicious .LNK files with hidden command-line arguments, threat actors can deceive users into executing these files, leading to unauthorized actions without the user’s knowledge.
Almost 1,000 malicious .lnk files were found abusing ZDI-CAN-25373
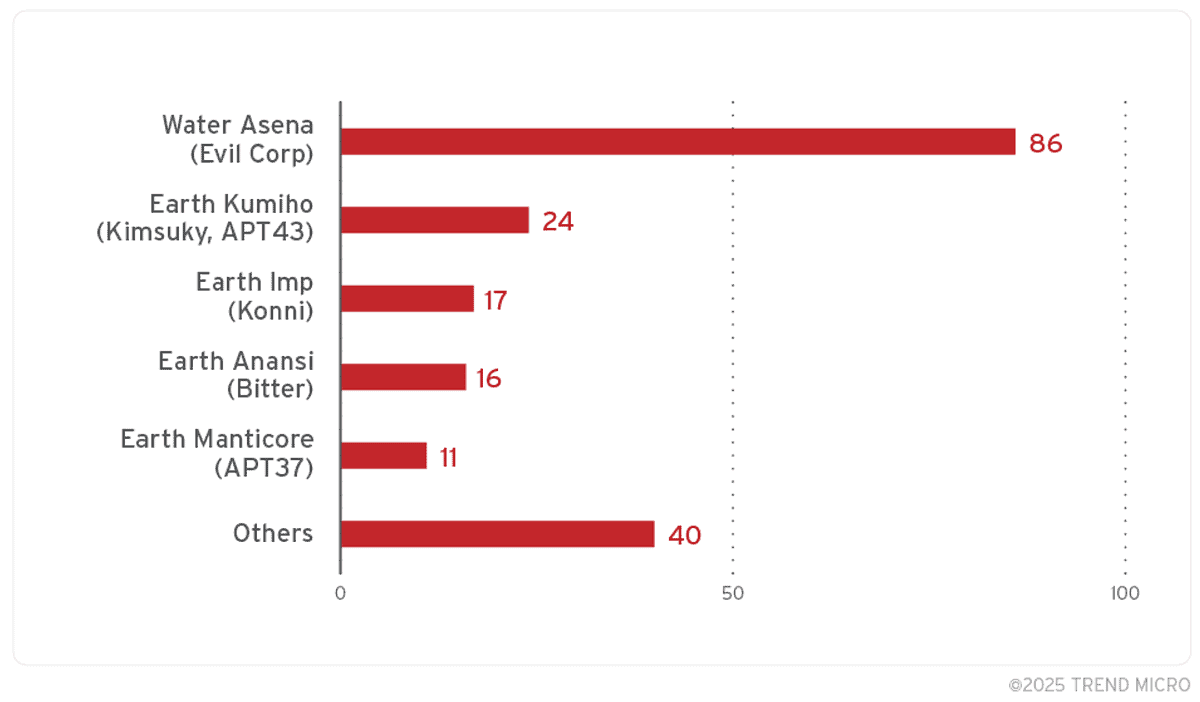
Trend Micro’s Zero Day Initiative (ZDI) has uncovered nearly a thousand .LNK file samples exploiting this vulnerability. Notably, prominent threat groups such as Evil Corp, Kimsuky, Konni, Bitter, and ScarCruft have leveraged this flaw to deploy malware like Lumma Stealer, GuLoader, and Remcos RAT. Targets have included government agencies, financial institutions, telecommunications providers, and defense organizations across countries like the United States, Canada, Russia, South Korea, Vietnam, and Brazil.
Microsoft hasn’t released a security patch
Despite this vulnerability’s severity and prolonged exploitation, Microsoft has classified it as “low severity” and currently does not plan to release a security patch:
Subsequently, we submitted a proof-of-concept exploit through Trend ZDI’s bug bounty program to Microsoft, who declined to address this vulnerability with a security patch.
The company recommends users exercise caution when downloading files from unknown sources and rely on security features like Microsoft Defender and Smart App Control to mitigate potential threats.
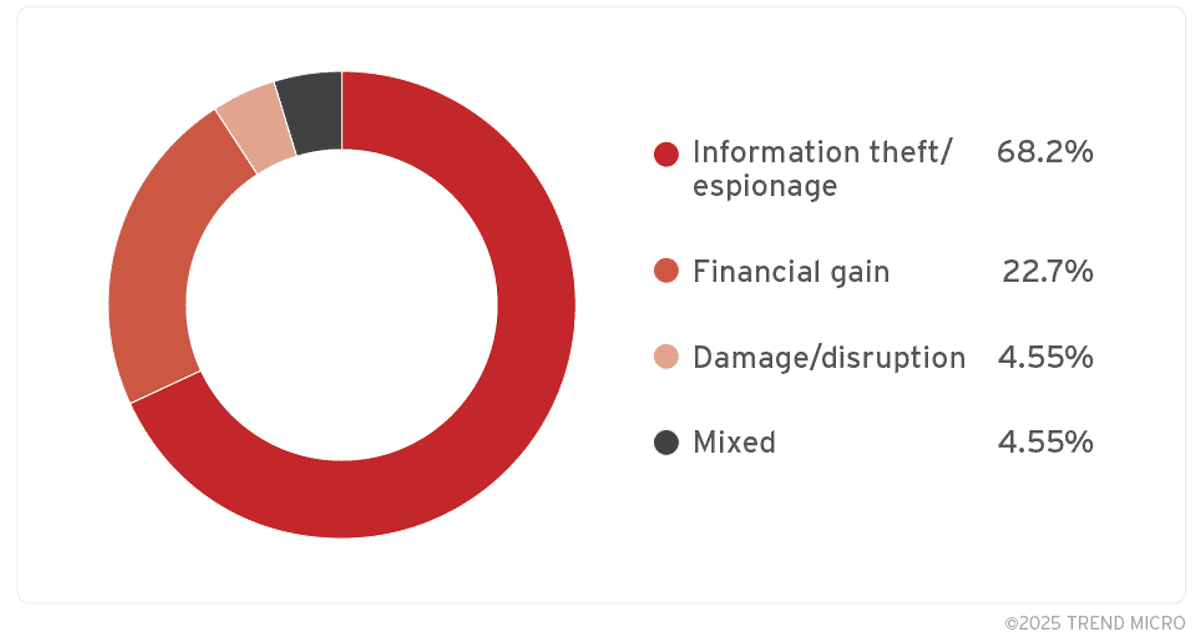
Given the absence of an official patch, users and organizations are advised to:
- Exercise Vigilance: Be cautious when interacting with unsolicited files, especially those received via email or downloaded from untrusted sources.
- Utilize Security Tools: Ensure that security software, such as Microsoft Defender, is active and up-to-date to detect and block potential threats exploiting this vulnerability.
- Implement Network Protections: Deploy network-level defenses to monitor and control the execution of .LNK files, reducing the risk of exploitation.
While Microsoft has not assigned this vulnerability a CVE identifier, Trend Micro continues to track it as ZDI-CAN-25373 and emphasizes the need for heightened awareness and proactive security measures to protect against potential attacks.





User forum
0 messages