Microsoft Defender for Endpoint can now detect unmanaged devices on your network
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more

Microsoft has announced that the ability to detect unmanaged devices such as employee phones or rogue hardware on your company network is now generally available in Microsoft Defender for Endpoint.
Microsoft says such devices introduce some of the greatest risks to an organization’s cybersecurity posture.
“The riskiest threat is the one you don’t know about. Unmanaged devices are literally one of your weakest links. Smart attackers go there first,” said David Weston, Microsoft Director of Enterprise and OS Security.
The new release offer the following new new capabilities:
- Discovery of endpoints and network devices connected to your corporate network
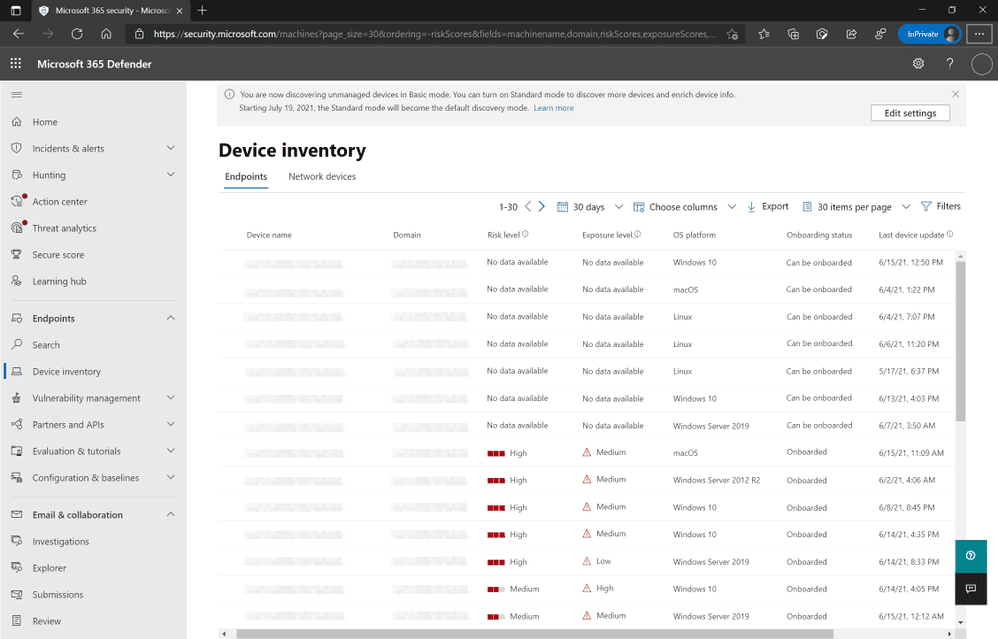
This capability provides Defender for Endpoint with the ability to discover unmanaged workstations, servers, and mobile endpoints (Windows, Linux, macOS, iOS, and Android) that haven’t been onboarded and secured. Additionally, network devices (e.g.: switches, routers, firewalls, WLAN controllers, VPN gateways and others) can be discovered and added to the device inventory using periodic authenticated scans of preconfigured network devices.
- Onboard discovered devices and secure them using integrated workflows
Once discovered, unmanaged endpoint and network devices connected to your networks can be onboarded to Defender for Endpoint. Integrated new workflows and new security recommendations in the threat and vulnerability management experience make it easy to onboard and secure these devices.
- Review assessments and address threats and vulnerabilities on newly discovered devices
Once endpoints and network devices have been discovered, assessments can be run using Defender for Endpoint’s threat and vulnerability management capabilities. These security recommendations can be used to address issues on devices helping to reduce an organization’s threat and risk exposure.
The new capabilities are enabled by default and is indicated by a banner that appears in the Endpoints\Device inventory section of the Microsoft 365 Defender console.
For more information please review the device discovery and network discovery documentations on Microsoft Docs.









User forum
0 messages