Dell's BIOS software open to remote exploit affecting 30 million laptops
2 min. read
Published on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
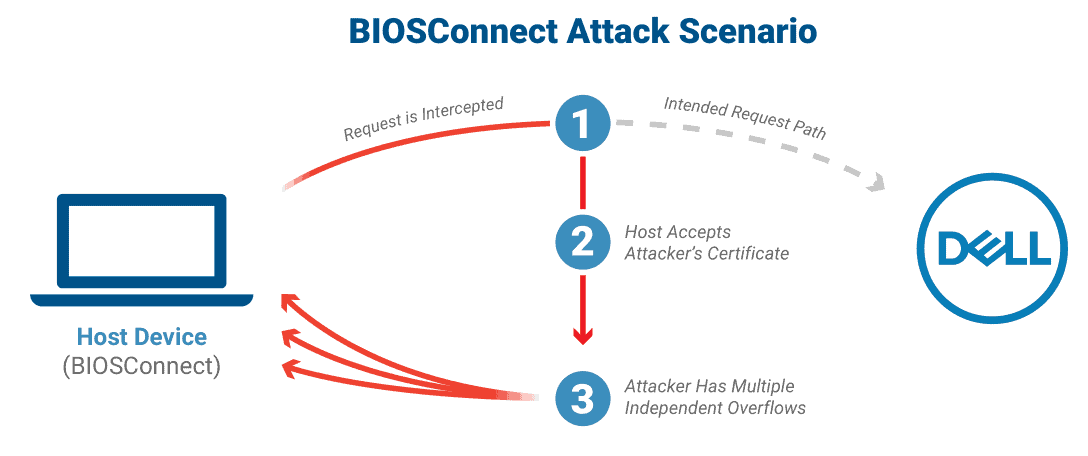
Security research Eclypsium has discovered that Dell’s remote BIOS update software is open to a man in the middle attack which allows attackers to remotely execute code within the BIOS of up to 129 different Dell laptop models.
“Such an attack would enable adversaries to control the device’s boot process and subvert the operating system and higher-layer security controls,” Eclypsium researchers explain.
Eclypsium says up to 30 million devices, which include consumer and business laptops, desktops, and tablets are affected.
At issue is the BIOSConnect feature, which is part of Dell’s SupportAssistant. This feature is pre-installed on most Dell Windows devices.
The service uses an insecure TLS connection from BIOS to Dell and has three overflow vulnerabilities which allow attackers to deliver any software they choose to devices.
Two of the overflow security flaws “affect the OS recovery process, while the other affects the firmware update process,” Eclypsium says. “All three vulnerabilities are independent, and each one could lead to arbitrary code execution in BIOS.”
The researchers say all the devices need to have their BIOS updated, and recommends Dell’s BIOSConnect feature not be used to do this.
Read Eclypsium’s report here and the complete list of affected device models in Dell’s advisory.
via BleepingComputer




User forum
0 messages