Best Hacking Tools for Windows - 10 Most Powerful Options
9 min. read
Updated on
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more
Are you looking for the best hacking tools for Windows to audit the security systems of your clients and servers? Your search ends here!
In this article, I’ve rounded up some of the best ethical hacking tools you must try out as a cybersecurity expert, website owner, and Windows server admin. I’ve also provided a handy how-to guide to demonstrate what you can achieve. Ready?
Best Hacking Tools for Windows
Find below a summary table for the best ethical hacking software for IT systems based on Windows OS and servers:
| Software Name | Usage | GUI | CLI | Expertise Level | Pricing |
| Nmap | Network security assessment | Yes | Yes | Intermediate | Free |
| John the Ripper | Password security auditing | No | Yes | High | Free |
| Burp Suite | Web vulnerability scanning | Yes | No | Intermediate | Paid |
| Metasploit Framework | Penetration testing | Yes | Yes | High | Free |
| Invicti | Application security testing | Yes | No | Intermediate | Paid |
| Wireshark | Network protocol analyzer | Yes | Yes | High | Free |
| Nessus | Assessing online vulnerability | Yes | Yes | Intermediate | Paid |
| Aircrack-ng | Wi-Fi network auditing | No | Yes | Intermediate | Free |
| SQLMap | Locating SQL injection flaws | No | Yes | Intermediate | Free |
| Nikto | Web scanning | No | Yes | Intermediate | Free |
Here’s a full review of the hacking tools mentioned in the table:
1. Nmap
Nmap is an open-source hacking software used in scanning networks for security assessment. This efficient tool is capable of mapping network topology and identifying potential vulnerabilities. Its powerful scripting engine supports versatile port scanning.
System admins use it for managing service upgrade schedules and monitoring service or host uptime. Some of its other highlighted features include:
- Robust host discovery
- Accurate version detection
- OS fingerprinting.
This software is available in both traditional command line and GUI versions.
Pros:
- This tool comes with comprehensive documentation in multiple languages.
- It can quickly scan large networks of hundreds of systems.
- It offers customized scripting to perform advanced tasks.
Cons:
- It performs the best against single hosts.
- Advanced features might be overwhelming for new users.
2. John the Ripper
As an ethical hacker, you can use John the Ripper to audit password security and recover passwords from Windows, Linux, Mac, and other operating systems.
This open-source application is widely used in penetration testing and security assessments. It supports hundreds of hash and cipher types. It also employs dictionary and brute-force attacks for quick results. If you’re also looking for the best keylogger to track passwords, this tool will fit in nicely.
You can also download the Hash Suite app for Windows PCs. It’s similar to John the Ripper and was created by one of its developers.
Pros:
- This is a fast password audit tool.
- It supports various password hash algorithms including Windows passwords.
- It can be integrated with other security tools.
Cons:
- Its scope is limited to password cracking.
- The initial setup and configuration might seem challenging to newbies.
3. Burp Suite
Burp Suite allows you to automatically identify various vulnerabilities in your website. If you’re a website security penetration tester you’ll want to use this tool to automate customized attacks and bug searches.
The software also helps you discover harder-to-find vulnerabilities at a high speed. It uses location fingerprinting techniques to scan modern web applications with fewer requests.
Pros:
- The software offers unparalleled protection against zero-day vulnerabilities.
- It allows custom configuration for scanning a particular type of vulnerability.
- It supports the detection of bugs such as asynchronous SQL injection and blind SSRF.
Cons:
- During intensive scanning, the tool can require significant system resources.
- It’s not the most novice-friendly solution.
4. Metasploit
Metasploit is a penetration testing framework that focuses on vulnerability verification and security assessment. It works as a platform for exploit development and execution.
It also has a built-in exploit database containing a large collection of exploits, payloads, and shellcodes.
Pros:
- The tool can be used to develop exploit codes against remote targets.
- It has an active user community that constantly provides updates and support.
- This software is also useful for developing IDS signatures.
Cons:
- It doesn’t have real-time exploit updates.
- The software only has a command-line interface.
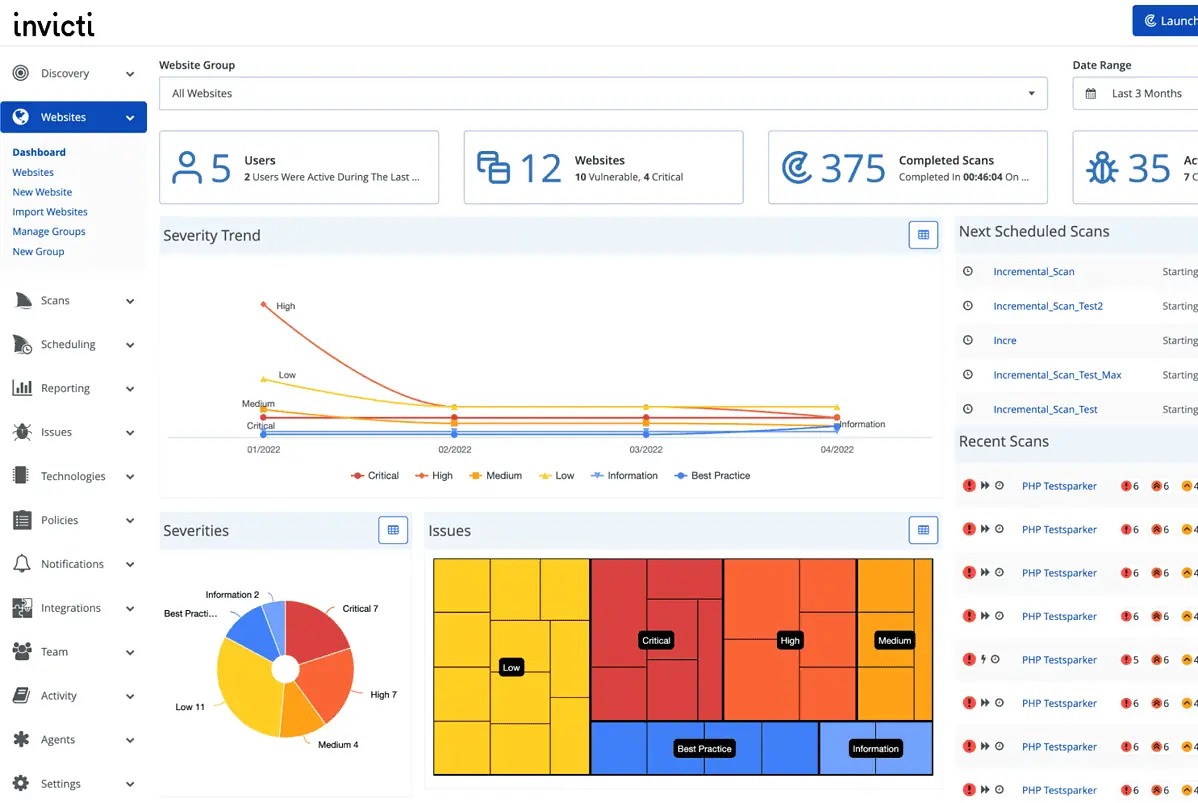
5. Invicti
If you’re looking for a reliable application security testing software, go for Invicti. Previously known as Netsparker, it can be used to automatically detect vulnerabilities.
This software is ideal for ethical hackers as it not only identifies the vulnerabilities but also assigns these for remediation. It offers accurate results without compromising on speed.
Pros:
- The tool can accurately detect web app vulnerabilities.
- It comes with a detailed dashboard.
- It uses unique dynamic and interactive scanning approaches to scan apps.
Cons:
- It might take a significant amount of system resources to function.
- This tool is relatively expensive.
6. Wireshark
Wireshark is a network protocol analyzer software that offers a microscopic view of your network. It can deeply inspect hundreds of protocols and the list keeps getting bigger. Besides having robust display filters, it offers coloring rules for the packet lists and performs rich VoIP analysis.
Pros:
- This tool supports decryption for many internet protocols like IPsec, Kerberos, SSL/TLS, etc.
- It lets you browse collected network data through GUI or TTY-mode TShark utility.
- It supports output data export in XML, CSV, PostScript, and plain text formats.
Cons:
- Beginners need to go through a steep learning curve.
- The software doesn’t offer real-time analysis.
7. Nessus
Modern-day cyberattacks need a state-of-the-art vulnerability assessment solution, like Nessus. This tool enables you to have complete visibility into your internet-connected attack surface. Thus, you can fortify your web apps and secure your cloud infrastructure.
Pros:
- This tool can detect weak passwords, misconfiguration, unpatched services, and other vulnerabilities.
- It lets you prioritize the threats that need attention first.
- It supports scheduled scanning mode.
Cons:
- The software might seem expensive to some organizations.
- It doesn’t provide any graphical reports.
8. Aircrack-ng
Aircrack-ng is a dedicated suite to audit wireless networks. It monitors Wi-Fi security, tests driver compatibility, and allows for heavy scripting. This solution is capable enough to crack WEP and WPA/WPA2-PSK encrypted networks.
Pros:
- This tool can perform a comprehensive wireless security assessment.
- It allows you to transfer data into text files.
- It has an active community that regularly updates the application.
Cons:
- It’s limited to Wi-Fi network security.
- Users need to have the technical experience to fully utilize its features.
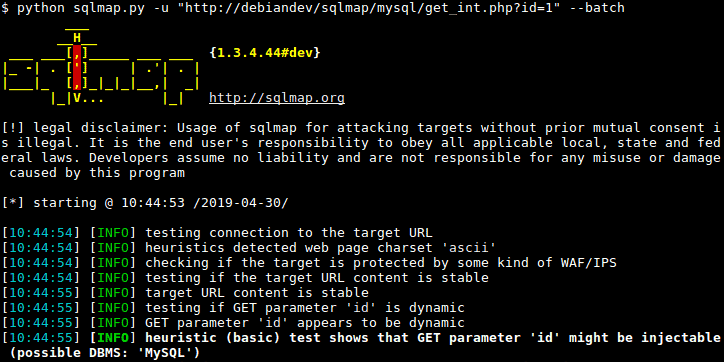
9. SQLMap
SQLMap is an open-source software that automatically exploits SQL Injection flaws. You can directly connect with specific databases and evaluate these against injection attacks. Its powerful detection engine can work as a penetration tester.
Pros:
- This tool supports six SQL injection techniques, including error-based and UNION query-based.
- It’s compatible with MySQL, Oracle, PostgreSQL, and many more.
- It allows customizable search for specific databases, tables, and columns.
Cons:
- The tool might be too complex for beginners.
- It doesn’t come with any GUI.
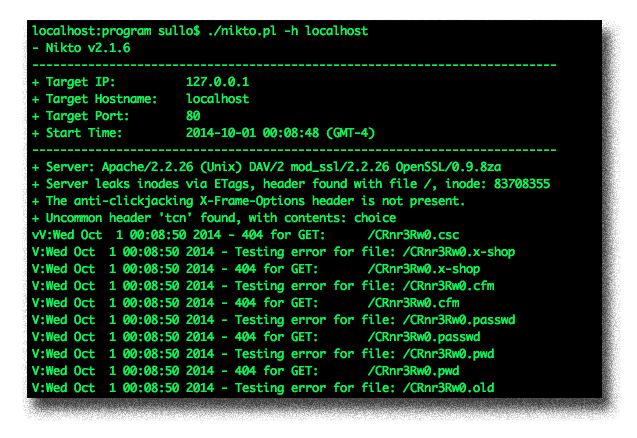
10. Nikto
Nikto is an open-source web and server scanner tool. It tests servers against potentially dangerous files, outdated server versions, and version-specific problems. It can also detect server configuration issues and outdated components. You can tune its scanning range to exclude or include an entire category of security vulnerability test.
Any IDS and IPS solutions will log Nikto’s activities. However, you can definitely check out LibWhisker’s anti-IDS protocol for Nikto if you want to test the IDS/IPS software you’re using.
Pros:
- The software supports SSL and full HTTP proxy.
- It generates reports reports in XML, HTML, plain text, NBE, and CSV.
- It has the ability to scan multiple ports of one server or multiple servers.
Cons:
- This software isn’t suitable for scanning systems or networks of large enterprises.
- Users might find the scan results to be overwhelming.
How Did I Choose the Best Hacking Tools for Windows?
The review process in selecting these tools involves meticulous testing across various cybersecurity scenarios. I scrutinized each tool listed above in simulated environments to assess its performance in detecting vulnerabilities.
My testing process also covers aspects such as user-friendliness, integration capabilities, and adaptability to diverse Windows operating system versions and server editions. I’ve also considered the legality and ethical standards before suggesting the best 10 tools above.
How To Use Hacking Tools?
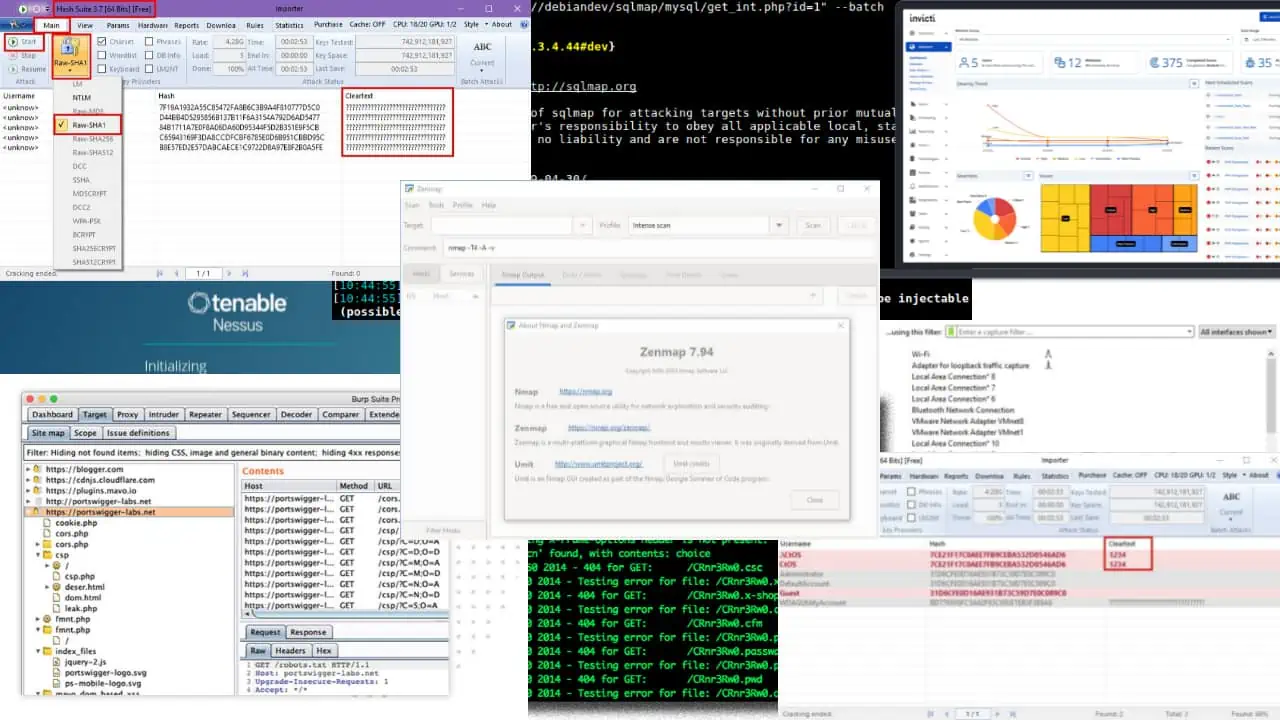
I’m going to show you how can you test the strength of the passwords you choose using the Hash Suite password cracker. Hash Suite is John the Ripper’s custom-built version for Windows.
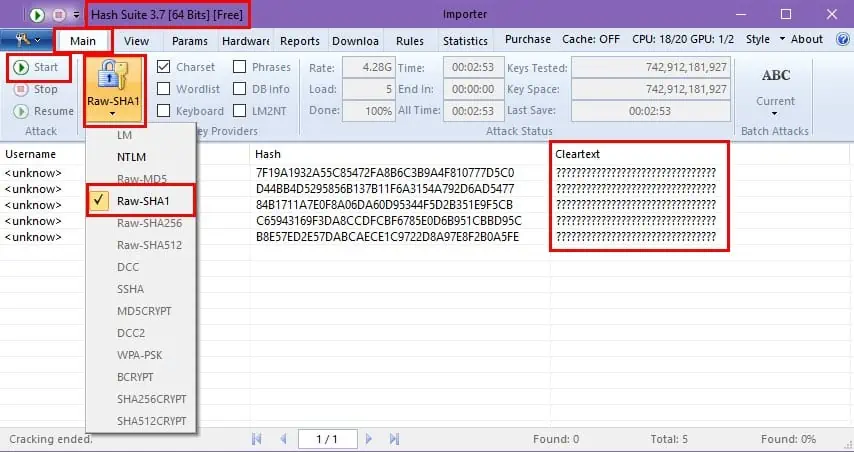
Here are the user names and their password hashcodes I’m going to try to crack:
| UserID | Hash Codes | Password |
| acme1 | 7f19a1932a55c85472fa8b6c3b9a4f810777d5c0 | ***** |
| acmeadmin1 | d44bb4d5295856b137b11f6a3154a792d6ad5477 | ***** |
| johndoe1 | 84b1711a7e0f8a06da60d95344f5d2b351e9f5cb | ***** |
| janedoe1 | c65943169f3da8ccdfcbf6785e0d6b951cbbd95c | ***** |
| tamal | b8e57ed2e57dabcaece1c9722d8a97e8f2b0a5fe | ***** |
Ideally, John the Ripper or Hash Suite will decode the hash codes into plaintext. The plaintext output is the actual password.
Here’s how you can crack passwords for vulnerability testing with Hash Suite:
- Download the Hash Suite Windows desktop app.
- Unzip the Hash_Suite_Free file.
- Go to the Hash_Suite_Free folder.
- Run the Hash_Suite_64 or Hash_Suite_32 EXE file.
- You should now see the Hash Suite desktop app with the Main tab as the default selection.
- Click the Format button on the Hash Suite ribbon menu and choose SHA1. This is the format for the hash codes I’ve chosen.
- You can choose another format depending on your hash code list.
- Now, click the Start button.
- On the Attack Status group, End In values show the ETA.
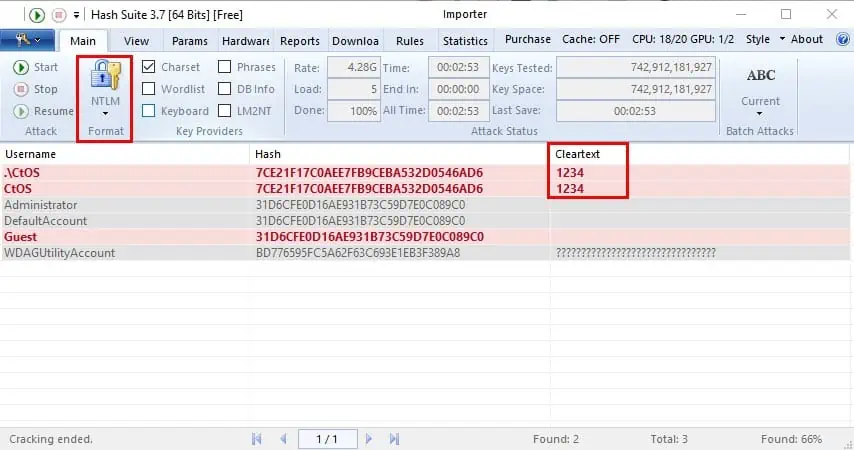
- Once done, Hash Suite reveals the password characters under the Cleartext column.
Since the passwords I’m using are strong, Hash Suite was unable to crack the passwords and the underlying hashcodes.
However, Hash Suite was able to crack simple Windows PC user account passwords.
By now, you should have explored the best hacking tools for Windows that you can use in various cybersecurity systems auditing projects. The above list includes ethical hacking tools from different aspects of digital systems like networking, password management, Wi-Fi networks, and so on.
Feel free to try them out and share your feedback in the comment box below.