Attackers now hide malicious Word files into PDF documents. Here's how to protect yourself

Cybersecurity experts have identified a sophisticated attack technique by which harmful Word files are embedded within PDF documents, evading traditional security measures. This technique is referred to as the MalDoc in PDF. Attackers can run malicious macros when the file is opened in Microsoft Word, infecting the target’s system.
How does MalDoc in PDF work?
An attack involves attaching a false MHTML (MHT) file embedded with macros to an otherwise pristine PDF file. Hybrid files can be directly opened in Microsoft Word with the appearance and feel of a PDF structure and signature. Once the macro capability is enabled, opening the document can cause arbitrary actions on the infected system when embedded scripts execute.
Traditional PDF analysis tools will typically not be able to detect malicious content in such hybrid files, as they appear to be normal PDFs. Antivirus software may also overlook the threat, misclassifying the file based on its PDF signature. However, specialized malicious Office macro analysis tools, such as OLEVBA, have proven helpful in detecting and extracting embedded macro code from these files.
How to protect against MailDoc in PDF
To counter this threat, security experts recommend installing custom YARA rules to detect the existence of both PDF signatures as well as Office document structures embedded in them:
The below is an example of a detection rule created using Yara rule. In this method, if an Excel file is stored in a PDF file, a warning screen is displayed when Excel starts up, stating that the file extension is different, and the file will not be opened in Excel unless the warning is accepted. Therefore, at the time of the release of this article, it is unlikely that Excel files are used for this technique.
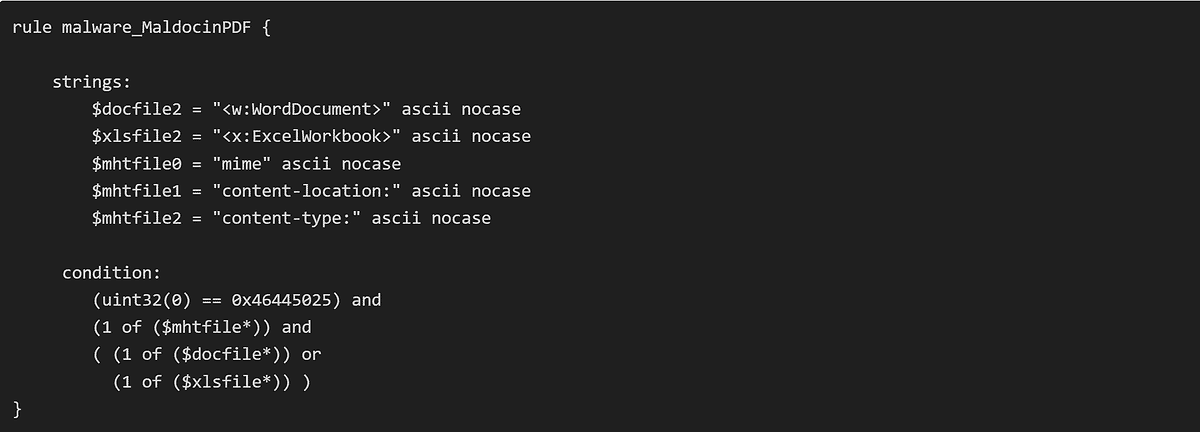
Additionally, turning off the macro execution by default within Microsoft Word can prevent the automatic running of potentially malicious scripts. Organizations must update their security controls to include scanning for such hybrid file types and conduct user awareness training to minimize risk exposure.
Read our disclosure page to find out how can you help MSPoweruser sustain the editorial team Read more



User forum
0 messages